难度1
Broadcast
题目
粗心的Alice在制作密码的时候,把明文留下来,聪明的你能快速找出来吗?
题解
估计是个签到题,task.py里面直接可以看见flag。
hidden key
题目
你可以找到合适的key吗?
from Crypto.Util.number import *
from secret import flag
import random
import hashlib
import os
key=os.urandom(8)
def rand(rng):
return rng - random.randrange(rng)
m=[]
random.seed(int(hashlib.md5(key).hexdigest(), 16))
for i in range(len(flag)):
rand(256)
xor=flag[i]^rand(256)
m.append(xor)
print(m)
print(bytes_to_long(key)>>12)
# [140, 96, 112, 178, 38, 180, 158, 240, 179, 202, 251, 138, 188, 185, 23, 67, 163, 22, 150, 18, 143, 212, 93, 87, 209, 139, 92, 252, 55, 137, 6, 231, 105, 12, 65, 59, 223, 25, 179, 101, 19, 215]
# 2669175714787937题解
输出的m数组是每一位flag与随机数异或后的结果,但是随机数是用种子生成的,我们可以直接用同样的种子生成随机数,然后逐个异或就可以获得原flag。
但是因为随机数种子被右移位12次,需要遍历查找正确的flag,先讲其左移位12次,并遍历填充右12位,逐个试探看能否破解正确flag即可。
from Crypto.Util.number import *
import random
import hashlib
import os
shifted_result=2669175714787937<<12
def rand(rng):
return rng - random.randrange(rng)
m= [140, 96, 112, 178, 38, 180, 158, 240, 179, 202, 251, 138, 188, 185, 23, 67, 163, 22, 150, 18, 143, 212, 93, 87, 209, 139, 92, 252, 55, 137, 6, 231, 105, 12, 65, 59, 223, 25, 179, 101, 19, 215]
for offset in range(2**12):
realflag=""
key = long_to_bytes(shifted_result+offset)
random.seed(int(hashlib.md5(key).hexdigest(), 16))
for i in range(42):
rand(256)
realflag+=chr(m[i]^rand(256))
if realflag.startswith("flag"):
print(realflag)baigeiRSA
题目
白给了,白给了,真白给!
import libnum
from Crypto.Util import number
from secret import flag
size = 128
e = 65537
p = number.getPrime(size)
q = number.getPrime(size)
n = p*q
m = libnum.s2n(flag)
c = pow(m, e, n)
print('n = %d' % n)
print('c = %d' % c)
# n = 88503001447845031603457048661635807319447136634748350130947825183012205093541
# c = 40876621398366534035989065383910105526025410999058860023908252093679681817257题解
简单RSA,只要分解N就可以了。
直接yafu分解.\yafu-x64.exe "factor(88503001447845031603457048661635807319447136634748350130947825183012205093541)"
from Crypto.Util import number
# from secret import flag
size = 128
e = 65537
n = 88503001447845031603457048661635807319447136634748350130947825183012205093541
c = 40876621398366534035989065383910105526025410999058860023908252093679681817257
p = 322368694010594584041053487661458382819
q = 274539690398523616505159415195049044439
# 计算 φ(n)
phi_n = (p - 1) * (q - 1)
# 计算私钥指数 d
d = libnum.invmod(e, phi_n)
# 解密明文
m = pow(c, d, n)
# 将明文转换为字符串
flag = libnum.n2s(m).decode()
print(flag)[简单] 初识RSA
题目
p和q藏起来了,你能帮我找到它们吗
from Crypto.Util.number import bytes_to_long,inverse,getPrime
from flag import flag
m = bytes_to_long(flag)
p = getPrime(1024)
q = getPrime(1024)
n = p*q
print(n)
e = 65537
c = pow(m,e,n)
pq = p*(q-1)
qp = q*(p-1)
print("c=",c)
print("n=",n)
print("pq=",pq)
print("qp=",qp)
'''
c= 8722269075970644434253339592758512788160408912707387632591552130175707843950684315083250494010055435391879036285103810263591951437829414438640307561645721347859659807138051841516634704123100270651976676182059252251162982609391666023674158274992400910869692389001622774140191223807887675081808561012755545464977015973615407965906513878979919700065923364884766974187303774330319143647840846354404070430118235352622445115153298578370521811697710289716188726587743282814946239856766713516166990341116198180068191759095913957606379780234116317390622824096667107736103270907349927467971817639795094030622157581511033950777
n= 10466186506773626671397261081802640650185744558208505628349249045496105597268556020207175016523119333667851114848452038431498926527983706092607207796937431312520131882751891731564121558651246025754915145600686076505962750195353958781726515647847167067621799990588328894365930423844435964506372428647802381074584935050067254029262890188260006596141011807724688556673520261743199388391094490191001701011230322653422314758778116196105077883955436582364267530633358016652912054880813710531145973799193443828969535902856467548523653920307742364119002349899553478815101092655897400295925170383678499125295006364960124859003
pq= 10466186506773626671397261081802640650185744558208505628349249045496105597268556020207175016523119333667851114848452038431498926527983706092607207796937431312520131882751891731564121558651246025754915145600686076505962750195353958781726515647847167067621799990588328894365930423844435964506372428647802381074488896197029704465200125337817646702009123916866455067019234171839614862660036737875747177391796376553159880972782837853473250804807544086701088829096838316550146794766718580877976153967582795248676367265069623900208276878140709691073369415161936376086988069213820933152601453587292943483693378833664901178324
qp= 10466186506773626671397261081802640650185744558208505628349249045496105597268556020207175016523119333667851114848452038431498926527983706092607207796937431312520131882751891731564121558651246025754915145600686076505962750195353958781726515647847167067621799990588328894365930423844435964506372428647802381074475956379708898904933143429835002718457573266164923043251954374464149976302585916538814746811455883837138715445492053610047383292461097590195481556557381952895539341802954749542143253491617052100969586396996063822508764438280468492894012685918249843558593322831683872737943676955669923498182824352081785243246
'''题解
已知:
- pq = p*(q - 1)=pq - p
- qp = q*(p - 1)=qp - q
- n = p*q
由 pq = pq - p 可得 p = n - pq ,由 qp = qp - q 可得 q = n - qp 。
from Crypto.Util.number import bytes_to_long, getPrime
e = 65537
n = 10466186506773626671397261081802640650185744558208505628349249045496105597268556020207175016523119333667851114848452038431498926527983706092607207796937431312520131882751891731564121558651246025754915145600686076505962750195353958781726515647847167067621799990588328894365930423844435964506372428647802381074584935050067254029262890188260006596141011807724688556673520261743199388391094490191001701011230322653422314758778116196105077883955436582364267530633358016652912054880813710531145973799193443828969535902856467548523653920307742364119002349899553478815101092655897400295925170383678499125295006364960124859003
pq = 10466186506773626671397261081802640650185744558208505628349249045496105597268556020207175016523119333667851114848452038431498926527983706092607207796937431312520131882751891731564121558651246025754915145600686076505962750195353958781726515647847167067621799990588328894365930423844435964506372428647802381074488896197029704465200125337817646702009123916866455067019234171839614862660036737875747177391796376553159880972782837853473250804807544086701088829096838316550146794766718580877976153967582795248676367265069623900208276878140709691073369415161936376086988069213820933152601453587292943483693378833664901178324
qp = 10466186506773626671397261081802640650185744558208505628349249045496105597268556020207175016523119333667851114848452038431498926527983706092607207796937431312520131882751891731564121558651246025754915145600686076505962750195353958781726515647847167067621799990588328894365930423844435964506372428647802381074475956379708898904933143429835002718457573266164923043251954374464149976302585916538814746811455883837138715445492053610047383292461097590195481556557381952895539341802954749542143253491617052100969586396996063822508764438280468492894012685918249843558593322831683872737943676955669923498182824352081785243246
# 计算p和q
p = n - pq
q = n - qp
phi_n = (p - 1) * (q - 1)
# 计算私钥指数 d
d = libnum.invmod(e, phi_n)
c= 8722269075970644434253339592758512788160408912707387632591552130175707843950684315083250494010055435391879036285103810263591951437829414438640307561645721347859659807138051841516634704123100270651976676182059252251162982609391666023674158274992400910869692389001622774140191223807887675081808561012755545464977015973615407965906513878979919700065923364884766974187303774330319143647840846354404070430118235352622445115153298578370521811697710289716188726587743282814946239856766713516166990341116198180068191759095913957606379780234116317390622824096667107736103270907349927467971817639795094030622157581511033950777
# 解密明文
m = pow(c, d, n)
# 将明文转换为字符串
flag = libnum.n2s(m).decode()
print(flag)难度2
flag_in_your_hand
题目
给了一个网页和一段JS脚本,输入值之后会给出flag。
题解
function getFlag() {
var token = document.getElementById("secToken").value;
ic = checkToken(token);
fg = bm(token);
showFlag()
}
function showFlag() {
var t = document.getElementById("flagTitle");
var f = document.getElementById("flag");
t.innerText = !!ic ? "You got the flag below!!" : "Wrong!";
t.className = !!ic ? "rightflag" : "wrongflag";
f.innerText = fg;
}核心函数是这两个函数,如输入正确,经过checkToken和bm两个函数处理之后,判断ic的值来给出正确的flag。
先看checkToken函数
function checkToken(s) {
return s === "FAKE-TOKEN";
}checkToken函数很简单,输入FAKE-TOKEN就会返回true给ic,但是测试之后发现不对,那就一定是其他的地方改变了ic的值。
检索js文件,发现只有下面这个函数会改变ic的值
function ck(s) {
try {
ic
} catch (e) {
return;
}
var a = [118, 104, 102, 120, 117, 108, 119, 124, 48,123,101,120];
if (s.length == a.length) {
for (i = 0; i < s.length; i++) {
if (a[i] - s.charCodeAt(i) != 3)
return ic = false;
}
return ic = true;
}
return ic = false;
}这个逻辑就很简单了,只需要把输入串和a构造满足条件即可,给出代码。
a = [118, 104, 102, 120, 117, 108, 119, 124, 48,123,101,120]
flag=""
for i in range(len(a)):
flag+=chr(a[i]-3)
print(flag)得到flag输入网页即可得到真实flag。
safer-than-rot13
题目
XMVZGC RGC AMG RVMG HGFGMQYCD VT VWM BYNO, NSVWDS NSGO RAO XG UWFN AF HACDGMVWF. AIRVFN AII AMG JVRRVC-XVMC, FYRBIG TVIZ ESV SAH CGQGM XGGC RVMG NSAC A RYIG TMVR NSG SVWFG ESGMG NSGO EGMG XVMC WCNYI NSG HAO FVRG IVMH JARG MVWCH NV NAZG NSGR VTT NV EAM. OVWM TIAD YF "CV NSYF YF CVN JMOBNV RO HGAM", YC IVEGMJAFG, EYNS WCHGMFJVMGF YCFNGAH VT FBAJGF, FWMMVWCHGH XO NSG WFWAI "TIAD" NAD ACH JWMIO XMAJGF. GCUVO.题解
看起来像是单表替换,直接一把梭。http://quipqiup.com/
0 -1.467 BROKEN MEN ARE MORE DESERVING OF OUR PITY, THOUGH THEY MAY BE JUST AS DANGEROUS. ALMOST ALL ARE COMMON-BORN, SIMPLE FOLK WHO HAD NEVER BEEN MORE THAN A MILE FROM THE HOUSE WHERE THEY WERE BORN UNTIL THE DAY SOME LORD CAME ROUND TO TAKE THEM OFF TO WAR. YOUR FLAG IS "NO THIS IS NOT CRYPTO MY DEAR", IN LOWERCASE, WITH UNDERSCORES INSTEAD OF SPACES, SURROUNDED BY THE USUAL "FLAG" TAG AND CURLY BRACES. ENJOY.按照文字提示,需要转换小写并用下划线替换空格,比较坑的一点是文字提示要用flag包裹,但是实际上不用,flag就是no_this_is_not_crypto_my_dear
告诉你个秘密
题目
636A56355279427363446C4A49454A7154534230526D6843
56445A31614342354E326C4B4946467A5769426961453067题解
先随波逐流一把梭,发现base16可以解出东西。
cjV5RyBscDlJIEJqTSB0RmhC
VDZ1aCB5N2lKIFFzWiBiaE0g再梭一把,base64可以解出东西
r5yG lp9I BjM tFhB
T6uh y7iJ QsZ bhM每一组在键盘上都可以围出一个字母,就是最终flag TONGYUAN。
你猜猜
题目
我们刚刚拦截了,敌军的文件传输获取一份机密文件,请君速速破解。
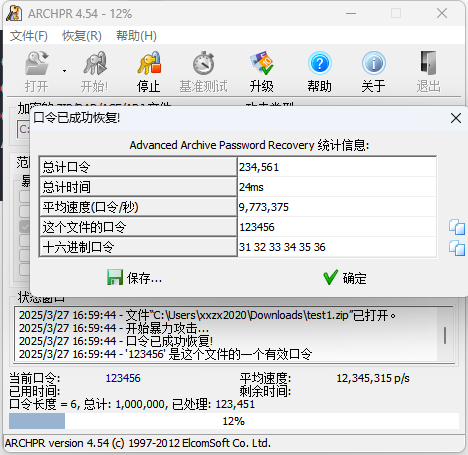
504B03040A0001080000626D0A49F4B5091F1E0000001200000008000000666C61672E7478746C9F170D35D0A45826A03E161FB96870EDDFC7C89A11862F9199B4CD78E7504B01023F000A0001080000626D0A49F4B5091F1E00000012000000080024000000000000002000000000000000666C61672E7478740A0020000000000001001800AF150210CAF2D1015CAEAA05CAF2D1015CAEAA05CAF2D101504B050600000000010001005A000000440000000000题解
504B开头,先保存成zip文件,打开发现有密码,试了一下不是伪加密,爆破一下得到flag。
cr3-what-is-this-encryption
题目
Fady同学以为你是菜鸟,不怕你看到他发的东西。他以明文形式将下面这些东西发给了他的朋友 p=0xa6055ec186de51800ddd6fcbf0192384ff42d707a55f57af4fcfb0d1dc7bd97055e8275cd4b78ec63c5d592f567c66393a061324aa2e6a8d8fc2a910cbee1ed9 q=0xfa0f9463ea0a93b929c099320d31c277e0b0dbc65b189ed76124f5a1218f5d91fd0102a4c8de11f28be5e4d0ae91ab319f4537e97ed74bc663e972a4a9119307 e=0x6d1fdab4ce3217b3fc32c9ed480a31d067fd57d93a9ab52b472dc393ab7852fbcb11abbebfd6aaae8032db1316dc22d3f7c3d631e24df13ef23d3b381a1c3e04abcc745d402ee3a031ac2718fae63b240837b4f657f29ca4702da9af22a3a019d68904a969ddb01bcf941df70af042f4fae5cbeb9c2151b324f387e525094c41 c=0x7fe1a4f743675d1987d25d38111fae0f78bbea6852cba5beda47db76d119a3efe24cb04b9449f53becd43b0b46e269826a983f832abb53b7a7e24a43ad15378344ed5c20f51e268186d24c76050c1e73647523bd5f91d9b6ad3e86bbf9126588b1dee21e6997372e36c3e74284734748891829665086e0dc523ed23c386bb520 他严重低估了我们的解密能力
题解
给出了p,q,e,c,RSA解
import libnum
from Crypto.Util import number
# from secret import flag
size = 128
e=0x6d1fdab4ce3217b3fc32c9ed480a31d067fd57d93a9ab52b472dc393ab7852fbcb11abbebfd6aaae8032db1316dc22d3f7c3d631e24df13ef23d3b381a1c3e04abcc745d402ee3a031ac2718fae63b240837b4f657f29ca4702da9af22a3a019d68904a969ddb01bcf941df70af042f4fae5cbeb9c2151b324f387e525094c41
p=0xa6055ec186de51800ddd6fcbf0192384ff42d707a55f57af4fcfb0d1dc7bd97055e8275cd4b78ec63c5d592f567c66393a061324aa2e6a8d8fc2a910cbee1ed9
q=0xfa0f9463ea0a93b929c099320d31c277e0b0dbc65b189ed76124f5a1218f5d91fd0102a4c8de11f28be5e4d0ae91ab319f4537e97ed74bc663e972a4a9119307
c=0x7fe1a4f743675d1987d25d38111fae0f78bbea6852cba5beda47db76d119a3efe24cb04b9449f53becd43b0b46e269826a983f832abb53b7a7e24a43ad15378344ed5c20f51e268186d24c76050c1e73647523bd5f91d9b6ad3e86bbf9126588b1dee21e6997372e36c3e74284734748891829665086e0dc523ed23c386bb520
# 计算 φ(n)
phi_n = (p - 1) * (q - 1)
n=p*q
# 计算私钥指数 d
d = libnum.invmod(e, phi_n)
print
# 解密明文
m = pow(c, d, n)
# 将明文转换为字符串
flag = libnum.n2s(m).decode()
print(flag)cr4-poor-rsa
题目
两个文件,一个是公钥,一个是密文
-----BEGIN PUBLIC KEY-----
ME0wDQYJKoZIhvcNAQEBBQADPAAwOQIyUqmeJJ7nzzwMv5Y6AJZhdyvJzfbh4/v8
bkSgel4PiURXqfgcOuEyrFaD01soulwyQkMCAwEAAQ==
-----END PUBLIC KEY-----
Ni45iH4UnXSttNuf0Oy80+G5J7tm8sBJuDNN7qfTIdEKJow4siF2cpSbP/qIWDjSi+w=公钥用openssl解密一下,得到N(Modulus)和E(Exponent)
Public-Key: (399 bit)
Modulus:
52:a9:9e:24:9e:e7:cf:3c:0c:bf:96:3a:00:96:61:
77:2b:c9:cd:f6:e1:e3:fb:fc:6e:44:a0:7a:5e:0f:
89:44:57:a9:f8:1c:3a:e1:32:ac:56:83:d3:5b:28:
ba:5c:32:42:43
Exponent: 65537 (0x10001)
Modulus=52A99E249EE7CF3C0CBF963A009661772BC9CDF6E1E3FBFC6E44A07A5E0F894457A9F81C3AE132AC5683D35B28BA5C324243
writing RSA key
-----BEGIN PUBLIC KEY-----
ME0wDQYJKoZIhvcNAQEBBQADPAAwOQIyUqmeJJ7nzzwMv5Y6AJZhdyvJzfbh4/v8
bkSgel4PiURXqfgcOuEyrFaD01soulwyQkMCAwEAAQ==
-----END PUBLIC KEY-----在线分解pq之后用rsa库推算private key并解密串。
; openssl rsa -pubin -text -modulus -in key.pub
import libnum
from Crypto.Util import number
# from secret import flag
import rsa
from base64 import b64decode
size = 128
e=65537
p=863653476616376575308866344984576466644942572246900013156919
q=965445304326998194798282228842484732438457170595999523426901
n=833810193564967701912362955539789451139872863794534923259743419423089229206473091408403560311191545764221310666338878019
b64c="Ni45iH4UnXSttNuf0Oy80+G5J7tm8sBJuDNN7qfTIdEKJow4siF2cpSbP/qIWDjSi+w="
# 计算 φ(n)
phi_n = (p - 1) * (q - 1)
n=p*q
# 计算私钥指数 d
d = libnum.invmod(e, phi_n)
privatekey = rsa.PrivateKey(n,e,d,p,q)
str = b64decode(b64c)
print(rsa.decrypt(str,privatekey).decode())
工业协议分析2
题目
在进行工业企业检查评估工作中,发现了疑似感染恶意软件的上位机。现已提取出上位机通信流量,尝试分析出异常点,获取FLAG。 flag形式为 flag{}
题解
流里面有疑似的字符串,16进制转字符后得到flag。
sherlock
题目
附件给了一个txt文件,夏洛克小说
题解
观察文本,发现有个别字母是大写字母,用正则把这部分筛选出来,发现是0和1构成的。
ZEROONEZEROZEROZEROZEROONEZEROZEROONEZEROZEROONEZEROZEROONEZEROONEZEROONEZEROONEZEROZEROZEROONEZEROONEZEROZEROONEONEZEROONEZEROZEROZEROZEROONEONEZEROONEZEROONEZEROONEZEROZEROZEROONEZEROZEROZEROONEONEZEROZEROONEONEONEONEZEROONEONEZEROONEONEZEROONEZEROZEROZEROZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROZEROONEZEROZEROZEROZEROONEONEZEROZEROONEONEZEROONEZEROONEONEONEONEONEZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROONEONEONEZEROZEROONEZEROONEONEONEONEONEZEROONEONEONEZEROZEROZEROZEROZEROONEONEZEROONEONEZEROZEROZEROZEROONEONEZEROONEZEROZEROZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROONEONEONEZEROZEROONEZEROONEONEONEONEONEZEROZEROONEONEZEROONEZEROONEZEROZEROONEONEZEROZEROZEROONEZEROZEROONEONEZEROONEONEONEZEROZEROONEONEZEROZEROONEONEZEROONEONEONEONEONEZEROONE替换成01之后二进制转字符可以得到flag。
crypto垃圾邮件
题目
常常收到垃圾邮件都不知道是什么东西,这次我一定要搞清楚
题解
用到了一个网站,https://www.spammimic.com/decode.shtml ,具体可以参考另一篇文章 spammimic加密
cat's gift
题目
如图所示,下面这只好心的猫猫给你送来了跨年礼物。由于礼物不好拿,所以猫猫把礼物平均分成了四份,但是其中一份不小心掉在地上散落成了无数片,变成了 1 - 1/3 + 1/5 - 1/7 + …
聪明的你能算出或猜出猫猫的礼物是什么吗?
flag示例: CatCTF{apple} CatCTF{banana}
提示:没思路的话可以问下这只猫猫有关Leibniz的事哦
题解
1 - 1/3 + 1/5 - 1/7 + …求极限是PI/4,所以礼物就是PI,CatCTF{pie}。
baigeiRSA2
题目
既然白给,就多给一点吧!
import libnum
from Crypto.Util import number
from functools import reduce
from secret import flag
n = 5
size = 64
while True:
ps = [number.getPrime(size) for _ in range(n)]
if len(set(ps)) == n:
break
e = 65537
n = reduce(lambda x, y: x*y, ps)
m = libnum.s2n(flag)
c = pow(m, e, n)
print('n = %d' % n)
print('c = %d' % c)
n = 175797137276517400024170861198192089021253920489351812147043687817076482376379806063372376015921
c = 144009221781172353636339988896910912047726260759108847257566019412382083853598735817869933202168题解
n是5个素数相乘,先factordb梭一下
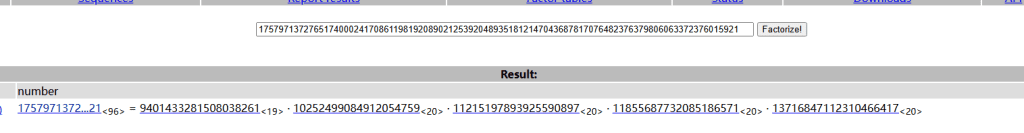
同理推算φ(n)=(q-1)*(p-1)*(r-1)*....
import libnum
from Crypto.Util import number
# from secret import flag
import rsa
from base64 import b64decode
n = 175797137276517400024170861198192089021253920489351812147043687817076482376379806063372376015921
c = 144009221781172353636339988896910912047726260759108847257566019412382083853598735817869933202168
n=9401433281508038261*10252499084912054759*11215197893925590897*11855687732085186571*13716847112310466417
phi_n=9401433281508038260*10252499084912054758*11215197893925590896*11855687732085186570*13716847112310466416
e = 65537
d = libnum.invmod(e, phi_n)
# 解密明文
m = pow(c, d, n)
# 将明文转换为字符串
flag = libnum.n2s(m).decode()
print(flag)二元一次方程组
题目
import libnum
from Crypto.Util import number
from secret import flag
size = 256
e = 65537
p = number.getPrime(size)
q = number.getPrime(size)
avg = (p+q)/2
n = p*q
m = libnum.s2n(flag)
c = pow(m, e, n)
print('n = %d' % n)
print('avg = %d' % avg)
print('c = %d' % c)
n = 5700102857084805454304483466349768960970728516788155745115335016563400814300152521175777999545445613444815936222559357974566843756936687078467221979584601
avg = 75635892913589759545076958131039534718834447688923830032758709253942408722875
c = 888629627089650993173073530112503758717074884215641346688043288414489462472394318700014742820213053802180975816089493243275025049174955385229062207064503题解
φ(n)=(q-1)*(p-1)=pq-(p+q)+1=n-2*avg+1
import libnum
from Crypto.Util import number
# from secret import flag
import rsa
from base64 import b64decode
e=65537
n = 5700102857084805454304483466349768960970728516788155745115335016563400814300152521175777999545445613444815936222559357974566843756936687078467221979584601
avg = 75635892913589759545076958131039534718834447688923830032758709253942408722875
c = 888629627089650993173073530112503758717074884215641346688043288414489462472394318700014742820213053802180975816089493243275025049174955385229062207064503
# 计算 φ(n)
phi_n=n-2*avg+1
# 计算私钥指数 d
d = libnum.invmod(e, phi_n)
# 解密明文
m = pow(c, d, n)
# 将明文转换为字符串
flag = libnum.n2s(m).decode()
print(flag)
babyFibo
题目
简单题,快做!
import os
import libnum
# from secret import flag
import sys
sys.setrecursionlimit(3000)
def fibo(n):
assert n >= 0
if n < 2:
return n
return fibo(n-1) + fibo(n-2)
s = fibo(1000)
m = libnum.s2n(flag+os.urandom((len(bin(s))-2)//8-len(flag)))
c = m^s
print(c)
s=43466557686937456435688527675040625802564660517371780402481729089536555417949051890403879840079255169295922593080322634775209689623239873322471161642996440906533187938298969649928516003704476137795166849228875题解
用斐波那契生成了一个第1000位的数,然后和密文异或得到C,直接异或解密即可。
第1000位要循环很久,直接网上可以搜到。
import os
import libnum
# from secret import flag
import sys
sys.setrecursionlimit(3000)
s=43466557686937456435688527675040625802564660517371780402481729089536555417949051890403879840079255169295922593080322634775209689623239873322471161642996440906533187938298969649928516003704476137795166849228875
c=43104378128345818181217961835377190975779804452524643191544804229536124095677294719566215359919831933542699064892141754715180028183150724886016542388159082125737677224886528142312511700711365919689756090950704
m=c^s
print(libnum.n2s(m))Xor很心疼你
题目
看了这么久题目了,Xor很心疼你,并打算考考你
# Python3
from secret import flag
import random
import base64
pool = 'qwertyuiopasdfghjklzxcvbnm1234567890QWERTYUIOPASDFGHJKLZXCVBNM'
r = random.randint(2, 250)
assert flag.startswith('hsctf{')
def generate(length):
return ''.join(random.choices(pool, k=length))
def f(x):
random.seed(x)
return random.getrandbits(8)
def encrypt(plaintext, key):
plaintext = list(map(ord, plaintext))
for _ in range(20):
key = f(key)
assert key != 0
for i in range(len(plaintext)):
key = f(key)
tmp = (key * r) % 251
assert tmp != 0 and key != 0
plaintext[i] = plaintext[i] ^ tmp
plaintext = bytes(plaintext)
return base64.b64encode(plaintext)
m = generate(random.randint(200, 300)) + flag + generate(random.randint(200, 300))
c = encrypt(m, random.getrandbits(128))
print(c)
# b'8OcTbAfL6/kOMQnC9v8SNmmSzvQMeGTT8vANM1T+7vIce2fo0fc2RnScrNxTSmeSyuMjMF//w8BWaXX91dsGcnvmreg0NQTw96ceVVXj3sQ3Znn51OU1S0bOyaMtNHTj36AcWFqewN4zRUXD6agGbAPE+tQtd3XG0doAa1Ll9fhcQ1zk0McTM1bv8PIQOAnn3vQ3UgLD3PsONXLs4KkXMnjTyMEQOFn/0uYVUwOY1PsleEHCyNopRVDr+Kc0e2PH9v0XNXfprfIPU3nw7KYTNX/G7twLSkHoyaUlQHXi3v02UHmdy/4iNgme3Pc8bgPp+tYWV1+YzPkXYkXM4ulUc27DrM4SNUPT2fQlckj1qP4Fal+YoPYJMlyZ8qhXfF3Y0tUDdUXl3vg0dFTi++VVOFfH/dgMS1ru9N8WU0HF9cUCTgPe+qVdSn/u7Mkda0GTw/QDcWPZ9KYGN2jSzfk0OVrMzt0yRHD64KMrUgPF2sFWcmP56KZSTAD61PUGeXrd49MgU1bL8OsVNWj91vIsalXwqf0qaWbwzv0lWETA4eElS3L99cYmU1nv9dRQTWbDyclScQTN6NIhV2j//+ZWbH7Z68kwM3Dy4dcUc1PQy8kRTl/4zcU9WGWfoakOMXuf69MXZQTEz+kJT1Dar8UN'
题解
先生成一个数字r是固定值。
生成一个数字key,然后每一轮用key作为种子生成下一个随机数key
使用key和r参与运算,进行加密。
key和r都不大,通过遍历的方式可以找出来key和r的值。
我们遍历r和key,用encrypt重新加密hsctf这个关键串,看看是否在密文中,即可确认r和key的值
from nt import environ
import random
import base64
from libnum import factorial_get_prime_pow
pool = 'qwertyuiopasdfghjklzxcvbnm1234567890QWERTYUIOPASDFGHJKLZXCVBNM'
# r = random.randint(2, 250)
# assert flag.startswith('hsctf{')
def generate(length):
return ''.join(random.choices(pool, k=length))
def f(x):
random.seed(x)
return random.getrandbits(8)
def encrypt(plaintext, key):
plaintext = list(map(ord, plaintext))
for i in range(len(plaintext)):
key = f(key)
tmp = (key * r) % 251
# assert tmp != 0 and key != 0
plaintext[i] = plaintext[i] ^ tmp
plaintext = bytes(plaintext)
return plaintext
c= b'8OcTbAfL6/kOMQnC9v8SNmmSzvQMeGTT8vANM1T+7vIce2fo0fc2RnScrNxTSmeSyuMjMF//w8BWaXX91dsGcnvmreg0NQTw96ceVVXj3sQ3Znn51OU1S0bOyaMtNHTj36AcWFqewN4zRUXD6agGbAPE+tQtd3XG0doAa1Ll9fhcQ1zk0McTM1bv8PIQOAnn3vQ3UgLD3PsONXLs4KkXMnjTyMEQOFn/0uYVUwOY1PsleEHCyNopRVDr+Kc0e2PH9v0XNXfprfIPU3nw7KYTNX/G7twLSkHoyaUlQHXi3v02UHmdy/4iNgme3Pc8bgPp+tYWV1+YzPkXYkXM4ulUc27DrM4SNUPT2fQlckj1qP4Fal+YoPYJMlyZ8qhXfF3Y0tUDdUXl3vg0dFTi++VVOFfH/dgMS1ru9N8WU0HF9cUCTgPe+qVdSn/u7Mkda0GTw/QDcWPZ9KYGN2jSzfk0OVrMzt0yRHD64KMrUgPF2sFWcmP56KZSTAD61PUGeXrd49MgU1bL8OsVNWj91vIsalXwqf0qaWbwzv0lWETA4eElS3L99cYmU1nv9dRQTWbDyclScQTN6NIhV2j//+ZWbH7Z68kwM3Dy4dcUc1PQy8kRTl/4zcU9WGWfoakOMXuf69MXZQTEz+kJT1Dar8UN'
c=base64.b64decode(c)
for r in range(2,251):
for key in range(1,2 ** 8):
brute_c=encrypt('hsctf{',key)
if brute_c in c:
print(r)
print(key)
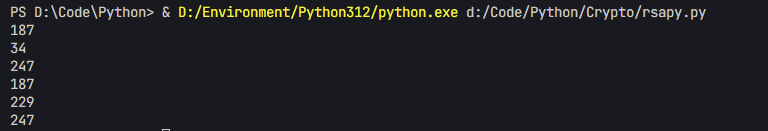
print(c.index(brute_c))得到两种可能性,r=187,key=34,真正字符串的起始位置是247
直接再次异或得到flag。
from nt import environ
import random
import base64
from libnum import factorial_get_prime_pow
pool = 'qwertyuiopasdfghjklzxcvbnm1234567890QWERTYUIOPASDFGHJKLZXCVBNM'
def generate(length):
return ''.join(random.choices(pool, k=length))
def f(x):
random.seed(x)
return random.getrandbits(8)
def decrypt(plaintext, key):
plaintext=list(plaintext)
for i in range(len(plaintext)):
key = f(key)
tmp = (key * r) % 251
# assert tmp != 0 and key != 0
plaintext[i] = plaintext[i] ^ tmp
plaintext = bytes(plaintext)
return plaintext
c= b'8OcTbAfL6/kOMQnC9v8SNmmSzvQMeGTT8vANM1T+7vIce2fo0fc2RnScrNxTSmeSyuMjMF//w8BWaXX91dsGcnvmreg0NQTw96ceVVXj3sQ3Znn51OU1S0bOyaMtNHTj36AcWFqewN4zRUXD6agGbAPE+tQtd3XG0doAa1Ll9fhcQ1zk0McTM1bv8PIQOAnn3vQ3UgLD3PsONXLs4KkXMnjTyMEQOFn/0uYVUwOY1PsleEHCyNopRVDr+Kc0e2PH9v0XNXfprfIPU3nw7KYTNX/G7twLSkHoyaUlQHXi3v02UHmdy/4iNgme3Pc8bgPp+tYWV1+YzPkXYkXM4ulUc27DrM4SNUPT2fQlckj1qP4Fal+YoPYJMlyZ8qhXfF3Y0tUDdUXl3vg0dFTi++VVOFfH/dgMS1ru9N8WU0HF9cUCTgPe+qVdSn/u7Mkda0GTw/QDcWPZ9KYGN2jSzfk0OVrMzt0yRHD64KMrUgPF2sFWcmP56KZSTAD61PUGeXrd49MgU1bL8OsVNWj91vIsalXwqf0qaWbwzv0lWETA4eElS3L99cYmU1nv9dRQTWbDyclScQTN6NIhV2j//+ZWbH7Z68kwM3Dy4dcUc1PQy8kRTl/4zcU9WGWfoakOMXuf69MXZQTEz+kJT1Dar8UN'
c=base64.b64decode(c)
r=187
key=34
index=247
flag=decrypt(c[247:],key)
print(flag)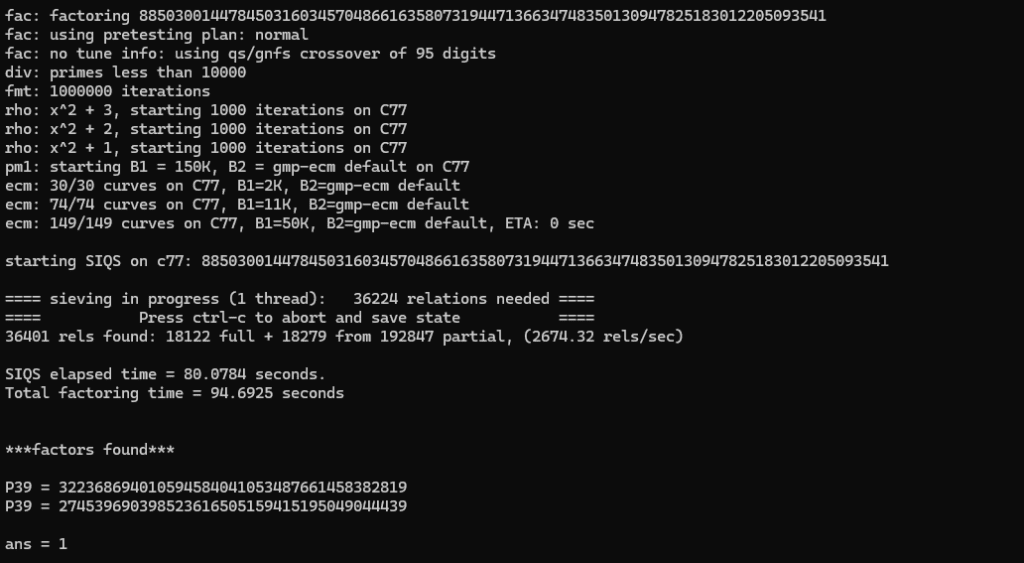


文章评论