Reverse
2
题解
Python打包程序,先“python pyinstxtractor.py 2.exe”
得到2.pyc,然后“uncompyle6 .\2.pyc”,得到关键代码
if __name__ == "__main__":
main()
turtle.mainloop()
print("fVJXNjE0ODBpM2RrZmNSVzYxNDgwaTNka01BSlVPe25oc20=")base64解码得到“}RW61480i3dkfcRW61480i3dkMAJUO{nhsm”
逆序得到“mshn{OUJAMkd3i08416WRcfkd3i08416WR}”
凯撒得到“mode1 #7: flag{HNCTFdw3b08416PKvydw3b08416PK}”
android1
题解
package com.gaga.test;
import android.os.Bundle;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
public class MainActivity extends AppCompatActivity {
private static byte[] CIPHER_BYTES;
private EditText edittextFlag;
static {
MainActivity.CIPHER_BYTES = new byte[0x20];
}
@Override // androidx.fragment.app.FragmentActivity
protected void onCreate(Bundle bundle0) {
super.onCreate(bundle0);
this.setContentView(layout.activity_main);
MainActivity.CIPHER_BYTES = new byte[]{0x75, 0x7F, 0x72, 0x74, 104, 94, 35, 0x71, 34, 0x7F, 0x76, 76, 82, 67, 34, 76, 85, 0x7F, 39, 0x74, 76, 33, 35, 34, 76, 87, 0x76, 0x20, 99, 50, 50, 110, 19};
this.edittextFlag = (EditText)this.findViewById(id.edittext_flag);
((Button)this.findViewById(id.button_check)).setOnClickListener((View view0) -> {
if(this.verifyFlag(this.edittextFlag.getText().toString())) {
Toast.makeText(this, "验证成功!", 0).show();
return;
}
Toast.makeText(this, "验证失败!", 0).show();
});
}
private boolean verifyFlag(String s) {
if(s != null && s.length() == 0x20) {
byte[] arr_b = s.getBytes();
return arr_b.length != 0x20 ? false : ((byte)(arr_b[0] ^ 19)) == MainActivity.CIPHER_BYTES[0];
}
return false;
}
}审计代码,发现是把数组与19异或。
s1=[117, 127, 114, 116, 104, 94, 35, 113, 34, 127, 118, 76, 82, 67, 34, 76, 85, 127, 39, 116, 76, 33, 35, 34, 76, 87, 118, 32, 99, 50, 50, 110, 19]
for i in range(0,len(s1)):
flag+=chr((s1[i])^19)
print(flag)
//AAAAAAAAAAAAAAAAAAAAflag{M0b1le_AP1_Fl4g_201_De3p!!} easyAPK
题解
ez_apk
题解
使用AES CBC PKCS5模式进行加密。秘钥是kkkeyyy404404404,向量是iviviviviviviviv。
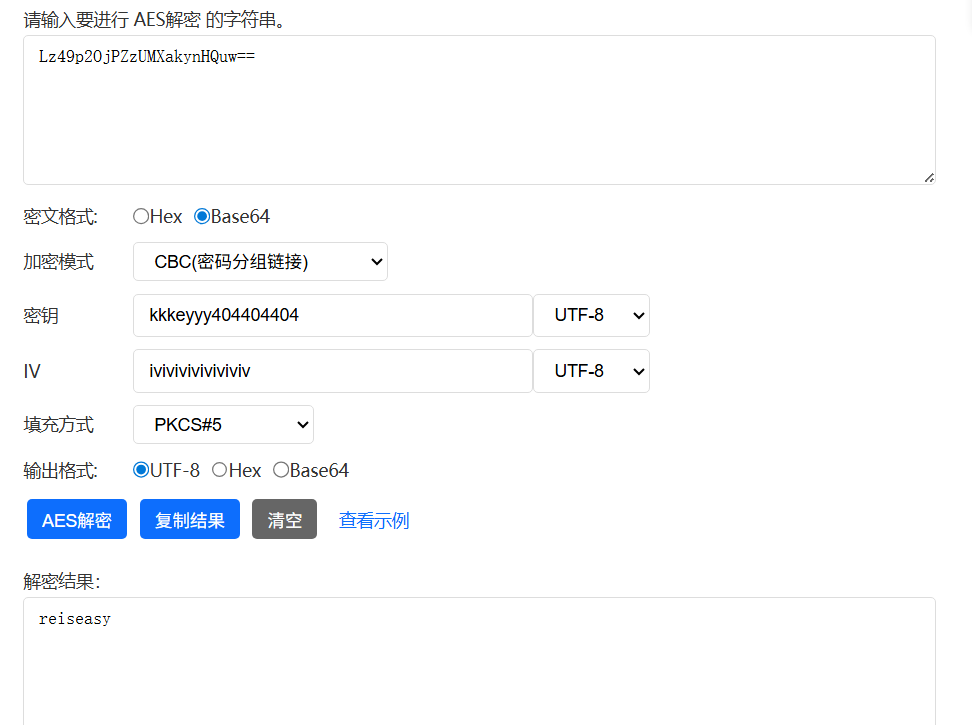
在线解密,得到密码为reiseasy,然后用admin,密码登录apk,得到图片
“3573534471566e756e45697274686a3673784c6d517533545a75516d6d347150646f4e78685658635338527a” 16进制转字符得到:“5sSDqVnunEirthj6sxLmQu3TZuQmm4qPdoNxhVXcS8Rz”
随波逐流一把梭,得到base58解码: HZNUCTF{4pk_5eem5_pretty_simp1e}
ez_apk
题解
private boolean checkcin(String s) {
byte[] arr_b = this.getString(0x7F0E0025).getBytes(); // string:key "aptxcony"
char[] arr_c = s.toCharArray();
char[] arr_c1 = new char[arr_c.length];
int v = 0;
while(v < arr_c.length) {
switch(arr_c[v]) {
case 0x5F:
case 0x7B:
case 0x7D: {
goto label_9;
}
}
if(arr_c[v] < 97 || arr_c[v] > 0x7A) {
break;
}
arr_c1[v] = (char)((arr_b[v % arr_b.length] - 97 + arr_c[v] - 97) % 26 + 97);
goto label_10;
label_9:
arr_c1[v] = arr_c[v];
label_10:
++v;
}
return this.cipher.equals(new String(arr_c1));
} protected void onStart() {
super.onStart();
String s = this.getString(0x7F0E0021); // string:cipher "f`vg\u007FvkXknxfznQv|gz|\u007F}c|G~bh{{x|\u007FVVFGX"
byte[] arr_b = s.getBytes();
for(int v = 0; v < s.length(); ++v) {
arr_b[v] = (byte)(arr_b[v] ^ v);
}
this.cipher = new String(arr_b);
}
可以在onStart里面得到初始字符串,并且这个串进行了一次异或操作。
after="f`vg\u007FvkXknxfznQv|gz|\u007F}c|G~bh{{x|\u007FVVFGX"
new_encrypted_text = ''
for i, s in enumerate(after):
new_encrypted_text += chr(ord(s) ^ i)
key = "aptxcony"
plain = []
for i, c in enumerate(new_encrypted_text):
if c in ['_', '{', '}']:
plain.append(c)
continue
if 'a' <= c <= 'z':
# 计算逆向偏移
key_char = ord(key[i % len(key)]) - ord('a')
cipher_char = ord(c) - ord('a')
plain_char = (cipher_char - key_char + 26) % 26
plain.append(chr(plain_char + ord('a')))
else:
plain.append(c)
print( ''.join(plain))
//flag{ez_crypto_algorithm_reverse_haha}

文章评论