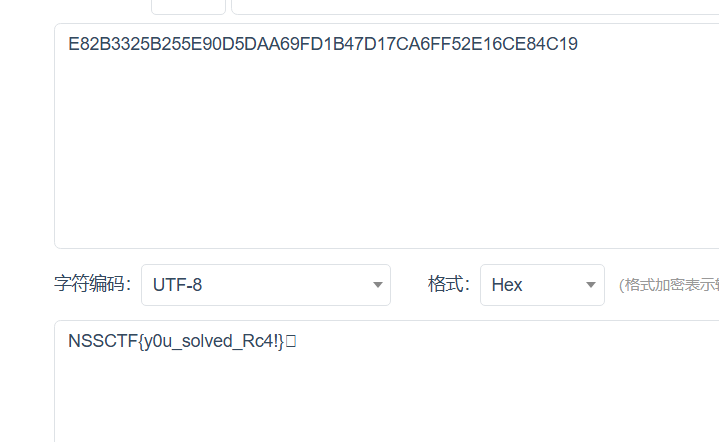
Rc4
题解
int __fastcall main(int argc, const char **argv, const char **envp)
{
unsigned int v3; // eax
unsigned int v4; // eax
char Str[112]; // [rsp+20h] [rbp-60h] BYREF
_BYTE v7[264]; // [rsp+90h] [rbp+10h] BYREF
int i; // [rsp+198h] [rbp+118h]
int v9; // [rsp+19Ch] [rbp+11Ch]
_main(argc, argv, envp);
printf("please input flag:");
scanf("%s", Str);
v3 = strlen("SakuraiCora");
rc4_init(v7, "SakuraiCora", v3);
v4 = strlen(Str);
rc4_crypt(v7, Str, v4);
v9 = 1;
for ( i = 0; i <= 23; ++i )
{
if ( Str[i] != enc_0[i] )
{
v9 = 0;
break;
}
}
if ( v9 )
printf("You get flag!\n");
else
printf("Wrong flag!\n");
return 0;
}key为“SakuraiCora”,初始串为enc_0
base64
题解
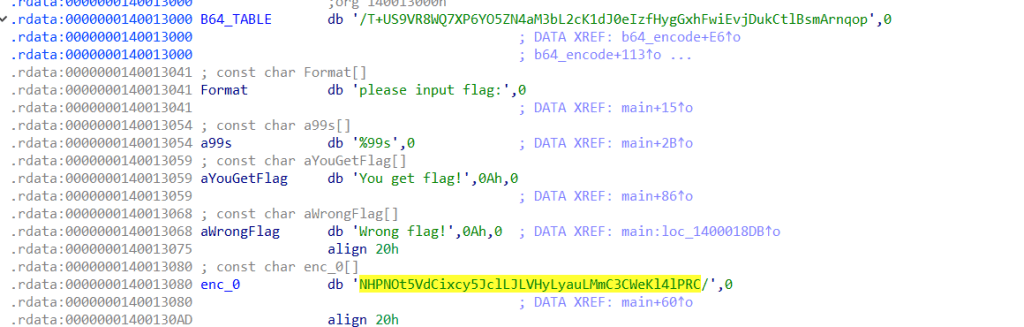
自定义码表的base64
easyenc
题解
先UPX脱壳
int __fastcall main(int argc, const char **argv, const char **envp)
{
__int64 v3; // rbx
__int64 v4; // rax
char v5; // al
char *v6; // rcx
_DWORD v8[10]; // [rsp+20h] [rbp-19h]
char v9; // [rsp+48h] [rbp+Fh]
_OWORD v10[3]; // [rsp+50h] [rbp+17h] BYREF
__int16 v11; // [rsp+80h] [rbp+47h]
v8[0] = 0x9FDFF04;
v8[1] = 0xB0F301;
v11 = 0;
v8[2] = 0xADF00500;
memset(v10, 0, sizeof(v10));
v3 = 0;
v8[3] = 0x5170607;
v8[4] = 0x17FD17EB;
v8[5] = 0x1EE01EA;
v8[6] = 0xFA05B1EA;
v8[7] = 0xAC170108;
v8[8] = 0xFDEA01EC;
v8[9] = 0x60705F0;
v9 = -7;
sub_140001064("%50s");
v4 = -1;
do
++v4;
while ( *((_BYTE *)v10 + v4) );
if ( v4 == 41 )
{
while ( 1 )
{
v5 = (*((_BYTE *)v10 + v3) ^ 0x32) - 86;
*((_BYTE *)v10 + v3) = v5;
if ( *((_BYTE *)v8 + v3) != v5 )
break;
if ( ++v3 >= 41 )
{
v6 = "you are right!";
goto LABEL_8;
}
}
v6 = "wrong!";
LABEL_8:
sub_140001010(v6);
}
return 0;
}逻辑是把V10异或之后-86,逆向操作即可,这里要注意:
- 逆向之后会超过字符的ascii码,要做取余操作。
- v8[2]是不足4字节的,前面要补0
s1=[0x04,0xFF,0xFD,0x09,0x01,0xF3,0xB0,0x00,0x00,0x05,0xF0,0xAD,0x07,0x06,0x17,0x05,0xEB,0x17,0xFD,0x17,0xEA,0x01,0xEE,0x01,0xEA,0xB1,0x05,0xFA,0x08,0x01,0x17,0xAC,0xEC,0x01,0xEA,0xFD,0xF0,0x05,0x07,0x06]
flag=""
for i in range(0,len(s1)):
flag+=chr(((s1[i]+86)^0x32)%128)
print(flag)
//hgame{4ddit1on_is_a_rever5ible_0perationnormal_upx
题解
int __fastcall main(int argc, const char **argv, const char **envp)
{
_BYTE v4[112]; // [rsp+20h] [rbp-90h] BYREF
__int64 v5; // [rsp+90h] [rbp-20h]
_BYTE v6[11]; // [rsp+98h] [rbp-18h]
int j; // [rsp+A4h] [rbp-Ch]
int v8; // [rsp+A8h] [rbp-8h]
int i; // [rsp+ACh] [rbp-4h]
_main(argc, argv, envp);
v5 = 0xE013C2E39292934LL;
*(_QWORD *)v6 = 0xF25091325091312LL;
*(_DWORD *)&v6[7] = 0x7020A0F;
printf("please input flag:");
scanf("%s", v4);
for ( i = 0; i <= 18; ++i )
v4[i] ^= 0x7Au;
v8 = 1;
for ( j = 0; j <= 18; ++j )
{
if ( v4[j] != v6[j - 8] )
{
v8 = 0;
break;
}
}
if ( v8 )
printf("You get flag!\n");
else
printf("Wrong flag!\n");
return 0;
}把输入先异或0x7A,然后在与V6比较
s1=[0x34,0x29,0x29,0x39,0x2E,0x3c,0x1,0x0E,0x12,0x13,0x09,0x25,0x13,0x09,0x25,0x0F,0x0A,0x02,0x07 ]
s2=[]
flag=""
for i in range(8,19+8):
s2.append(s1[i-8])
for i in range(0,len(s2)):
flag+=chr(s2[i]^0x7A)
print(flag)
//NSSCTF{this_is_upx}flag-where
题解
int __cdecl main_0(int argc, const char **argv, const char **envp)
{
char v4; // [esp+0h] [ebp-E4h]
int j; // [esp+D0h] [ebp-14h]
int i; // [esp+DCh] [ebp-8h]
__CheckForDebuggerJustMyCode(&unk_1022035);
MessageBoxW(0, &Text, &Caption, 0);
sub_10110C3(std::cin, byte_101F3F8);
for ( i = 0; i < 34; ++i )
{
key[i] = (dword_101CC30[i] ^ byte_101F044[i % 6]) - 114;
byte_101F5F0[i] = byte_101F000[key[i]];
}
for ( j = 0; j < 34; ++j )
{
if ( byte_101F3F8[j] != byte_101F5F0[j] )
exit(0);
sub_1011127("Correct!!!", v4);
}
return 0;
}把输入和byte_101F5F0进行比较
byte_101F5F0是把dword_101CC30和byte_101F044进行异或,得到下表,然后在byte_101F000里面查表。
byte_101F000的值为:abcdefghiABCDEFGHIJKLMNjklmn0123456789opqrstuvwxyzOPQRSTUVWXYZ{}_

byte_101F044的值为:ciallo
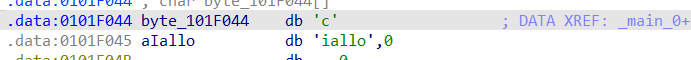
dword_101CC30的值为:[0xEB,0xC1,0xC9,0x11,0xC5,0xEF,0xD3,0x17,0x17,0x1F,0xF2,0x17,0x1B,0x13,0xEC,0x14,0xDE,0x15,0xFF,0xDB,0xC6,0x1A,0x1E,0xE4,0xE8,0xCB,0xD3,0xC4,0x16,0xE3,0xFA,0xE2,0x17,0xDD]
s1="abcdefghiABCDEFGHIJKLMNjklmn0123456789opqrstuvwxyzOPQRSTUVWXYZ{}_"
s2=""
dd=[0xEB,0xC1,0xC9,0x11,0xC5,0xEF,0xD3,0x17,0x17,0x1F,0xF2,0x17,0x1B,0x13,0xEC,0x14,0xDE,0x15,0xFF,0xDB,0xC6,0x1A,0x1E,0xE4,0xE8,0xCB,0xD3,0xC4,0x16,0xE3,0xFA,0xE2,0x17,0xDD]
c="ciallo"
for i in range(0,34):
s2+= s1[(dd[i]^ord(c[i%6]))-114]
print(s2)
//NSSCTF{Debugging_is_Really_Simple}

文章评论