Analyze network traffic using Wireshark to identify DanaBot initial access, deobfuscate malicious JavaScript, and extract IOCs like IPs, file hashes, and execution processes.
Scenario
The SOC team has detected suspicious activity in the network traffic, revealing that a machine has been compromised. Sensitive company information has been stolen. Your task is to use Network Capture (PCAP) files and Threat Intelligence to investigate the incident and determine how the breach occurred.
Questions
Q1.Which IP address was used by the attacker during the initial access?
62.173.142.148

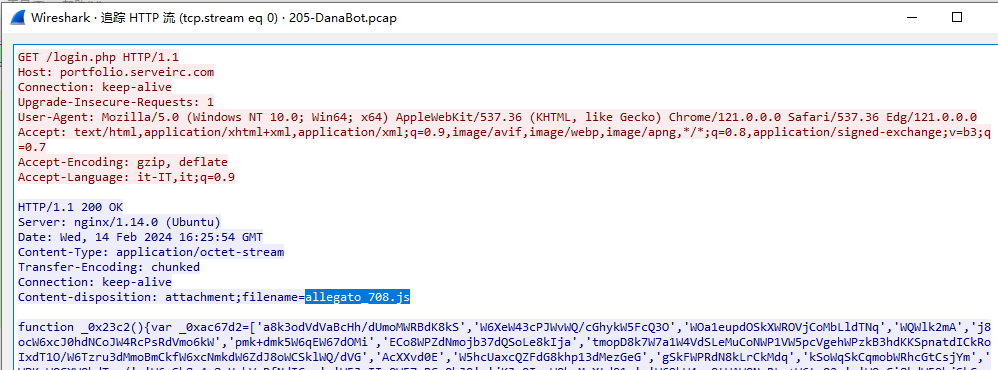
Q2.What is the name of the malicious file used for initial access?
追踪HTTP流,得到文件名allegato_708.js
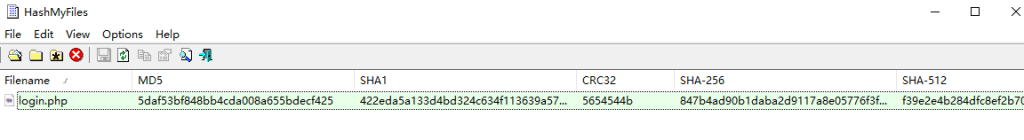
Q3.What is the SHA-256 hash of the malicious file used for initial access?
导出恶意文件,计算哈希847b4ad90b1daba2d9117a8e05776f3f902dda593fb1252289538acf476c4268
Q4.Which process was used to execute the malicious file?
用于执行脚本的windows程序为wscript.exe
Q5.What is the file extension of the second malicious file utilized by the attacker?
分析流可以得到答案为resources.dll
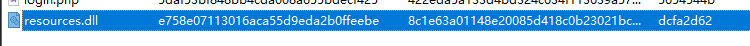
Q6.What is the MD5 hash of the second malicious file?
导出恶意文件,计算MD5为e758e07113016aca55d9eda2b0ffeebe
文章评论