Scenario
Reconstruct a multi-stage intrusion by analyzing network traffic, memory, and malware artifacts using Wireshark, Volatility, and VirusTotal, mapping findings to MITRE ATT&CK.
PCAP Analysis
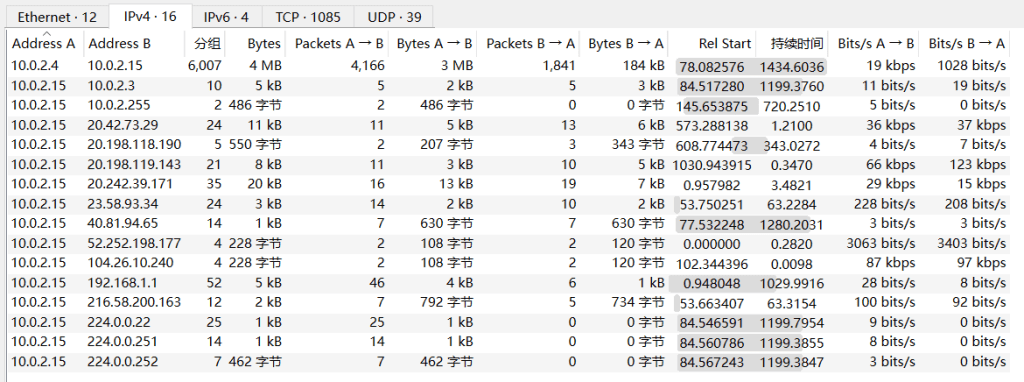
Q1.After flooding the IIS host with rapid-fire probes, the attacker reveals their origin. Which IP address generated this reconnaissance traffic?
10.0.2.4
Q2.Zeroing in on a single open service to gain a foothold, the attacker carries out targeted enumeration. Which MITRE ATT&CK technique ID covers this activity?
T1046
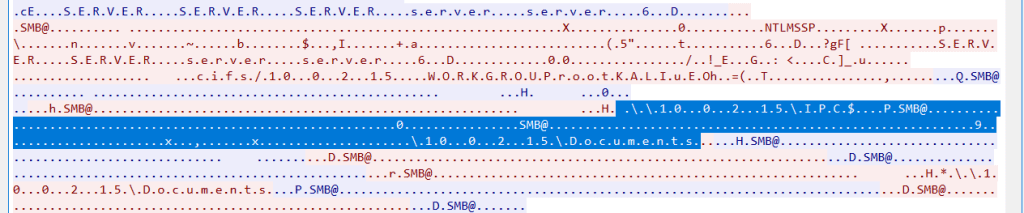
Q3.While reviewing the SMB traffic, you observe two consecutive Tree Connect requests that expose the first shares the intruder probes on the IIS host. Which two full UNC paths are accessed?
\10.0.2.15\Documents,\10.0.2.15\IPC$
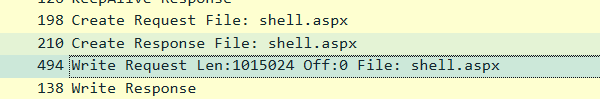
Q4.Inside the share, the attacker plants a web-accessible payload that will grant remote code execution. What is the filename of the malicious file they uploaded, and what byte length is specified in the corresponding SMB2 Write Request?
shell.aspx,1015024
Q5.The newly planted shell calls back to the attacker over an uncommon but firewall-friendly port. Which listening port did the attacker use for the reverse shell?
4443
Memory Dump Aanlysis
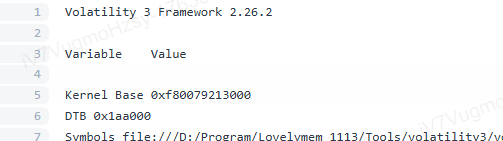
Q6.Your memory snapshot captures the system’s kernel in situ, providing vital context for the breach. What is the kernel base address in the dump?
0xf80079213000
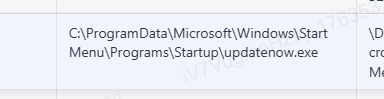
Q7.A trusted service launches an unfamiliar executable residing outside the usual IIS stack, signalling a persistence implant. What is the final full on-disk path of that executable, and which MITRE ATT&CK persistence technique ID corresponds to this behaviour?
通过MemProcFS查看进程信息,可以看到可疑程序
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\updatenow.exe
恶意程序放在StartUp,符合T1547 Boot or Logon Autostart Execution
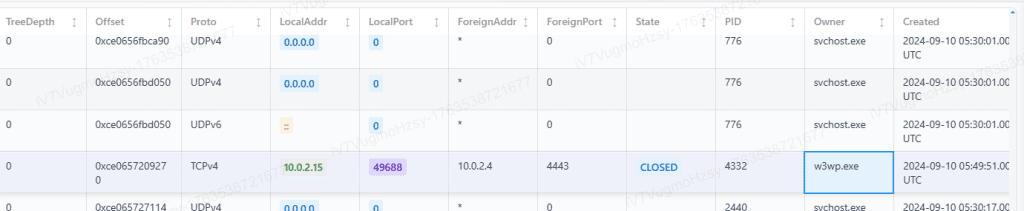
Q8.The reverse shell’s outbound traffic is handled by a built-in Windows process that also spawns the implanted executable. What is the name of this process, and what PID does it run under?
使用vol3.netscan,可以看到可疑监听。
答案为w3wp.exe,4332
Malware Sample Analysis
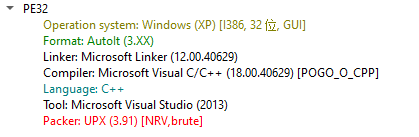
Q9.Static inspection reveals the binary has been packed to hinder analysis. Which packer was used to obfuscate it?
UPX
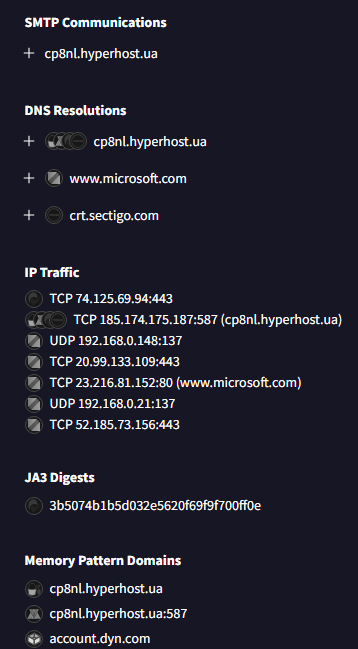
Q10.Threat-intel analysis shows the malware beaconing to its command-and-control host. Which fully qualified domain name (FQDN) does it contact?
用https://www.virustotal.com/分析,可以看到关联的域名为 cp8nl.hyperhost.ua
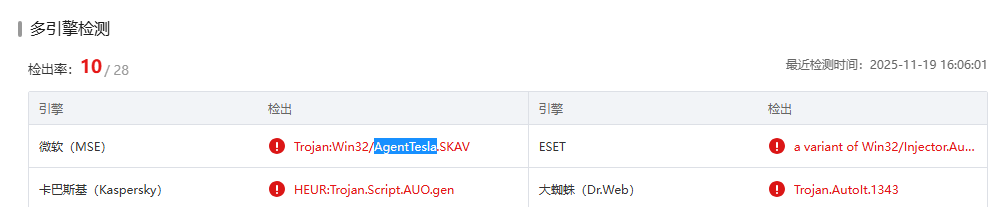
Q11.Open-source intel associates that hash with a well-known commodity RAT. To which malware family does the sample belong?
用微步沙箱检测,可以发现是AgentTesla
文章评论